
What Is Phishing - How To Prevent It
Phishing definitionPhishing is a type of cyberattack where cybercriminals use deceptive emails to lure you into giving away sensitive information. This information is then used to access important accounts which can result in identity theft and major financial loss. As phishing attacks increase in frequency and sophistication, they represent one of the biggest security risks for companies. |
Table of Contents
- Phishing attacks are on the rise
- Common features of phishing emails
- Phishing emails are often directed at employees
- What is a phishing kit?
- Famous phishing attacks
- Types of phishing
Phishing attacks are on the rise
Phishing attacks are showing no signs of slowing down. In 2020, phishing was the most common type of cybercrime and incidents nearly doubled in frequency from the previous year. On a global scale, 75% of organizations around the world experienced some kind of phishing attack in 2020.
There’s no doubt that the pandemic has changed the landscape for businesses by creating uncertainty and spurring new work habits such as remote work. Coupled with the availability of phishing kits making it easier than ever for cybercriminals to launch attacks, companies are faced with the perfect storm.
In this blog post, we’ll unpack what phishing is, the key features of an attack and the types of phishing you must be aware of. Then, we´ll get into what you can do to keep your company from becoming a phishing statistic.
Common features of phishing emails
Most people know that emails from the “Nigerian prince” offering you a huge sum of money is a phishing attack. However, when cybercriminals use tactics to exploit your trust and cause no feelings of alarm, even the savviest people fall prey to phishing attacks! Let’s look at the typical features of a phishing email:
- The email has bad grammar and spelling mistakes. The most obvious sign of a phishing email is incorrect use of grammar and bad spelling. Most companies use autocorrect and spell-checking tools to outgoing emails, so be wary the moment you receive an email ridden with mistakes.
- The email appears wildly unusual. If the request made in the email is out of the ordinary and not the norm in your company, be skeptical. One example could be someone in your IT department emailing you about the installation of a program when this type of activity is usually handled in some other way.
- The email demands urgent action. Phishing emails often use threats or have a sense of urgency that causes you to react quickly before thinking rationally. In fact, the top five subject lines for phishing attacks in 2019 included the words urgent, request, important, payment or attention.
- The email contains suspicious attachments. Phishing emails typically contain malicious attachments or hyperlinks to malicious websites. One impulsive click later, and your device is infected, or you have handed over personally identifiable information, credit card details or passwords to the cybercriminal.
- The email is too good to be true. Like the Nigerian prince example, if the email encourages you to click on a link or open an attachment to claim a reward of some nature, it’s most likely a phishing attempt. If something sounds too good to be true, it’s probably because it is.
Phishing emails are often directed at employees
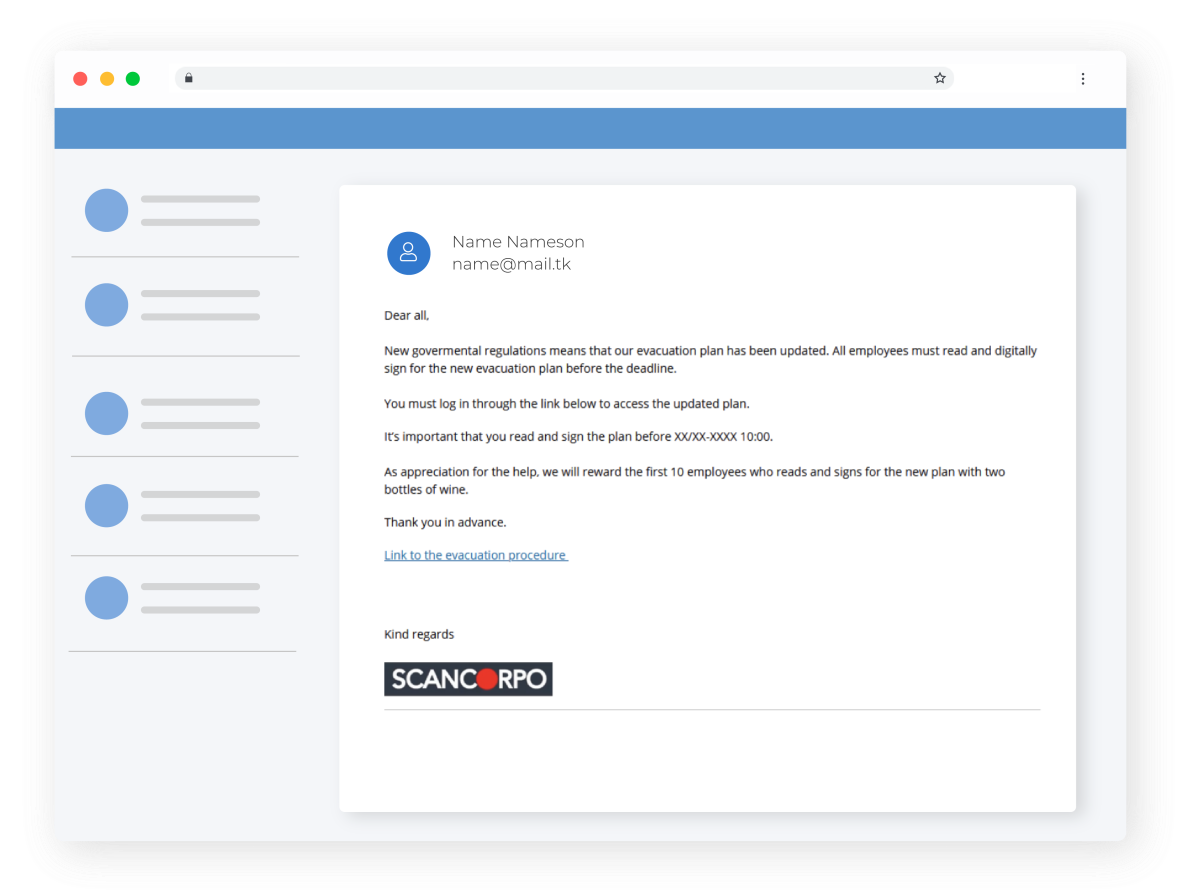
Cybercriminals tend to target the “weakest link” in the company, and without proper cyber security training, this will be your employees. Below is an example of a phishing email designed to take advantage of your employees’ trust and respect for authority. The email informs the employees of a “new evacuation plan” due to changed governmental regulations, and the employee is given a tight deadline to read and sign the plan by clicking the embedded hyperlink.
What is a phishing kit?
One of the reasons phishing attacks are on the rise is due to the availability of phishing kits. A phishing kit is a collection of software tools that makes it easy for cybercriminals, no matter their technical skills, to launch phishing campaigns. This is because the kits typically come complete with email templates, graphics and scripts that can be used to create convincing imitations of legitimate websites. As long as phishing kits are available on the dark web, phishing attacks are only likely to continue.
In addition to phishing kits, new AI technology makes phishing easier than ever. For instance, we asked ChatGPT to write us a phishing email, and got several well-written email templates we could send out - and cybercriminals can do the same thing.
Famous phishing attacks
Some phishing attacks make the headlines. The examples below illustrate how even the most tech savvy companies are victims of phishing emails - but more importantly, they show that the attacks could have been prevented if the companies had been more proactive in terms of building awareness around phishing.
A few years back, Facebook and Google fell prey to a phishing attack costing more than $100 million. A cybercriminal set up a fake company pretending to be a computer parts vendor affiliated with the tech giants and sent phishing emails to specific employees invoicing them for goods and services.
Another example is Sony Pictures, where employees received phishing emails appearing to come from Apple. Victims were prompted to enter their Apple ID into a fake form, and from here the attacker was able to figure out their Sony network login information. The attack cost the company more than 100 terabytes of company data, including financial records and customer data.

Types of phishing
Spear phishing, vishing, smishing – the list goes on. Phishing has evolved into many types. These tend to differ based on the target of the attack and the method used to carry out the attack. However, what they all have in common is the same end goal of acquiring sensitive information from the victim. Let’s break down the different types of phishing attacks:
- Smishing
- Vishing
- CEO fraud
- Spear phishing
- Whaling
- Barrel phishing
- Pharming
- Angler phishing
Smishing - phishing over text messaging
Smishing is basically phishing through text messaging. Similar to phishing, the text message has a sense of urgency and appears to come from a trusted entity. It will contain a URL link that takes you to a phishing tool prompting you to disclose private information. Here is an example of a VISA credit card smishing attack.
Vishing - voice phishing over phone calls
Have you ever received a phone call from someone pretending to be Microsoft? Then you’ve been exposed to vishing or voice phishing. While you may think “what sane person would fall for something like that”, a little spoofing of the caller ID and some persuasion later, you’d be surprised at how many people are convinced to install software that is really malware.
CEO fraud - pretending to be a company executive
CEO fraud, also known as executive phishing, is a type of cybercrime where the attacker pretends to be the CEO, CFO or another company executive over email. It works because it exploits your trust in authority, causing you to comply with their request without thinking twice.
Spear phishing - attacks targeted at specific employees
Spear phishing is a targeted form of phishing. Rather than sending out generic mass emails, the attacker will conduct research to craft fraudulent messages that appeal to a specific individual or group within an organization. While this requires more work for the cybercriminal, it leads to higher success rates as people let their guard down when the email appears to come from someone who knows them.
Whaling - attacks aimed at senior executives
Whaling, or whale phishing, is a form of spear phishing aimed at the “big fish” like CEOs or other high-profile individuals. The cybercriminal will take advantage of the publicly available information about these persons to tailor the phishing email. For example, a whaling email might state that the company is facing legal action or is the subject of reputational harm due to a recent public event or action taken by the executive.
Barrel phishing - sending one “innocent” email before the phishing email
Also called “double-barreling”, this tactic involves sending two separate emails where the first is the bait and the second is the email containing the malicious attachment. The first email may appear to come from your colleague and read “Hello, are in you in the office? I need a quick favor”. The purpose of this benign email is to establish trust and credibility, causing you to let your guard down. Then, the second follow-up email ticks in, sounding something like “Hi again, could you please review this report ASAP”. This email will contain a malicious link taking you to a spoof website.
Pharming
Pharming is where the cybercriminal unknowingly redirects your website request to a website that looks like the real thing, like your bank’s website. This way, the cybercriminal is able to capture your login data and can use this to gain access to your account. Unlike phishing where the attack occurs via electronic communication, pharming occurs directly in the browser. How does this work? In simple terms, the cybercriminal manipulates the domain name system (DNS), which is the system that connects web browsers to websites. For this reason, this form of attack is extremely sophisticated and difficult to recognize.
Angler Phishing
Angler phishing operates on social media. Here cyber-criminals make a fake social media account on e.g., Facebook, Twitter, or Instagram. The fake accounts will mirror the identity of the attacked company by using the same name and pictures. The hope is that people who are upset won’t realise that it isn’t a valid account they are communicating with and for this reason the fraud can be difficult to recognize. Normally, the victims of angler phishing are unsatisfied customers, and the attacks begin when a customer complains on social media. The purpose of angler phishing is to lure users into giving away sensitive information.
How to prevent phishing
So how to not fall for the phish? Two specific measures that help protect your company against phishing attacks include sandboxing and pen-testing with simulations. However, the reality is that humans are the ones being targeted by phishing attempts, and therefore humans must be the primary defense against them! Therefore, creating awareness around phishing and instilling a good security culture in your company is the first thing that needs to happen to prevent phishing attacks.
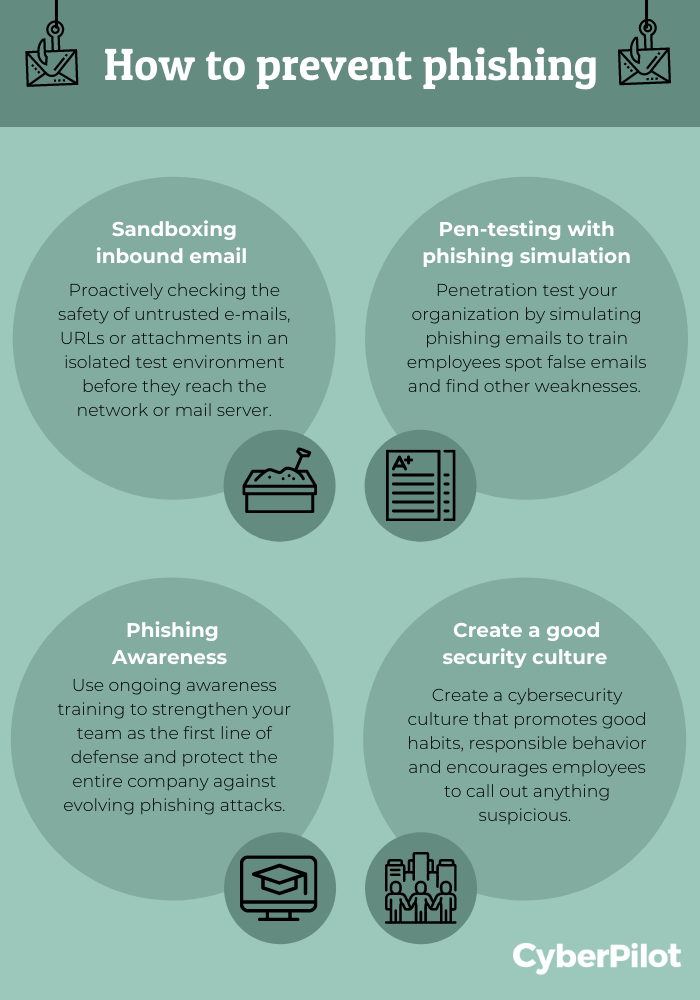
Sandboxing inbound email
“Sandboxing” is a proactive defense technique your IT security department can implement. It involves checking the safety of untrusted emails, URLs or attachments in an isolated test environment, before they reach your network or mail server. This technique provides an added layer of protection on top of the traditional filters that scan inbound emails.
Pen-testing with phishing simulation
Penetration testing, or pen-testing, is a security training exercise that tests your organization's preparedness against phishing. One way to do this is through simulated phishing attacks where your employees can practice their skills in spotting false emails. You can implement this exercise on your own, or work with an external training partner, depending on your goals. Based on the results, you can identify weak spots and devise strategies to further educate your employees.
Phishing Awareness
When you learn to spot the signs of phishing, you can better protect yourself and your company against attacks. Therefore, phishing awareness is key when it comes to prevention. However, a one-off crash course is not enough; as phishing attacks continue evolving, continuous training is essential to create an aware team. In fact, by combining simulations with on-going awareness training, you are empowering your team to become a strong first line of defense. Awareness training can take place through digital e-learning or physical teaching, or a mixture of both.
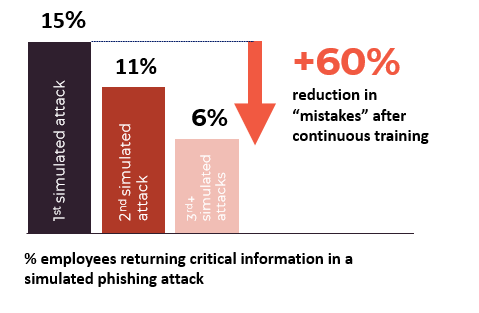
Our research shows that after continuous awareness training and phishing testing, users had a 50% reduction in mistakes during a simulated phishing attack.
Create a good security culture
Last but not least, instill a cybersecurity culture that promotes secure behaviors and empowers people to call out if something smells phishy. To help you get started, we have created a guide to creating a strong security culture based on the latest science and research. For instance, make sure you have a process in place in the event of a cyberattack, and that your team knows who to go to. Establishing this process and defining roles and expectations is one of many benefits of running a phishing simulation.
Additionally, encourage your team to always ask for help if they are in doubt and to not be afraid of making mistakes. This way, team members feel “safe” to report if the damage is done and a phishing email has been clicked. The result is that appropriate actions can be taken faster, and the damage is significantly reduced.
Finally, reward team members who report phishing emails, perhaps through showcasing a “catch of the day”. Also, to help your team practice good digital habits and be on alert, download our free cyber security posters to hang around your office!
Final words
In this blog post, we’ve outlined what phishing is and why it is one of the biggest security threats companies face today. We’ve learned that phishing comes in all shapes and sizes and that anyone in the organization can be targets of phishing attacks. For this reason, creating awareness around phishing through cyber security training has never been more important. By securing the human layer, you are significantly reducing the chances of your company becoming the phisherman’s latest catch!
People also asked
What does phishing mean?
Phishing is a type of cyber attack where attackers impersonate trustworthy entities through fraudulent emails, texts, or websites to trick individuals into revealing sensitive information such as login credentials, financial data or personal details, which are then used for malicious purposes.
What are the different types of phishing?
There are several types of phishing, including spear phishing, whaling, vishing, and smishing. Spear phishing targets a specific individual, while whaling targets high-profile individuals. Vishing uses phone calls, and smishing uses text messages to trick people into divulging personal information or downloading malware.
What happens when you get phished?
When you fall for a phishing scam, you may unknowingly provide sensitive information, such as login credentials, credit card numbers, or personal details, to cybercriminals. They can then use this information for fraudulent activities, such as identity theft, financial fraud, or spreading malware.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.







