The terms vishing and smishing may sound a little funny at first but they are serious forms of cybercrimes carried out via phone calls and text messages. You have probably heard of phishing which is a broad term that describes fraudelent activities and cybercrimes. Phishing involves cybercriminals targeting people via email, text messages and phonecalls by posing as legitimate institutaions to lure individuals into sharing personal information. In this blogpost we’ll talk about how smishing and vishing work, how to identify the signs, reduce the risks of attacks and what to do if you fall victim. We’ll cover what you need to know about vishing first, and then we’ll dive into smishing.
Table of Content
Scam texts are the new normal
The Ofcom report reveals that 71% of the 2000 UK adults surveyed had received a scam text message in the last three months, while 44% recieved a phone call with a recorded message and 41% were targetted with a live phone call from a scammer. The report also found that landline calls continued to be a threat for older people, with 61% of over-75s saying they had received a potential scam call. Different kinds of phishing attacks are getting more and more popular for cyber criminials.
What is vishing?
Vishing is a type of cybercrime that involves criminals stealing personal information through phone calls, it is also known as phone phishing. Cybercriminals call their victims and convince them to share their personal information such as credit card details, passwords and addresses. Some cybercriminals use strong and forceful language and others suggest they are helping the victim to avoid criminal charges. Another common tactic is to leave threatening voicemails that tell the victim to call back immediately, or they risk being arrested, having bank accounts shut down, or worse.
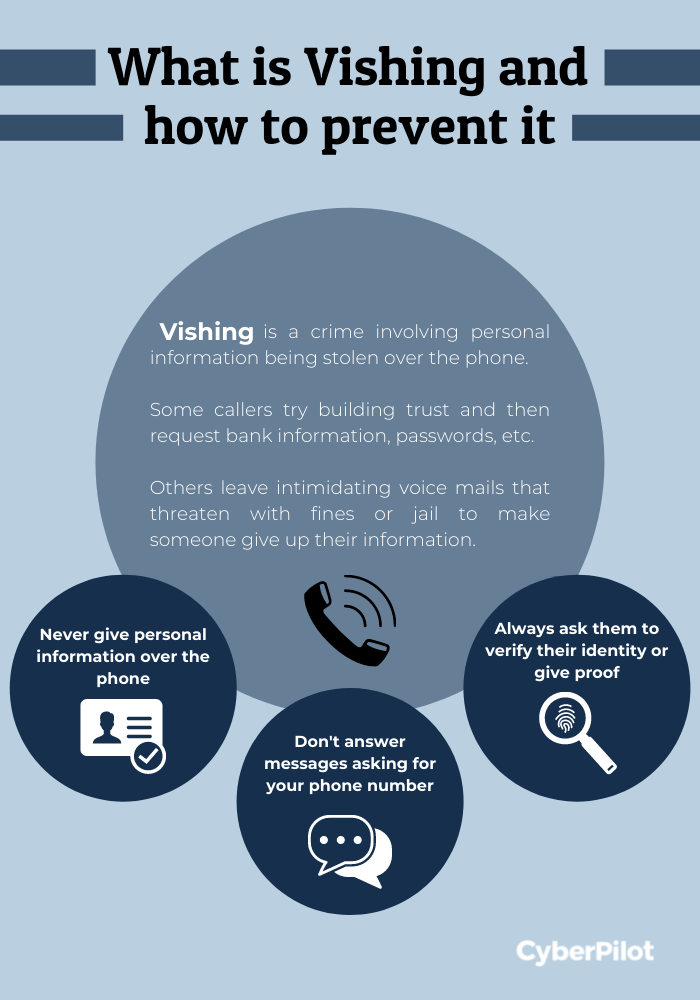
How does vishing work?
There are several steps cybercriminals take for a vishing attack to be successful. The first step is for cybercriminals to get their victim's phone number. They usually do this by sending phishing emails that prompt the victim to reply with their phone number, or by using specialized software that finds phone numbers according to area code. If the phishing attack is successful, the attacker gains the victims trust and the victim is expecting a call, in this case it is unlikely that the victim suspects an attack. Once the cybercriminal has the victim on the phone, they will try to convince the victim to reveal personal information, such as their bank account. Attackers succeed in these situations by appealing to their victims through trust and fear.
Examples of vishing attacks
There are several different types of vishing attacks. Here are some of the most common types that you should be aware of.
Bank Impersonation Fraud
Vishing attackers may impersonate your bank or credit card company to commit fraud. While impersonating the bank staff member, the cybercriminals might tell the victim their account is under threat and they need to make payments to a “safe account”. They might ask for online banking details so they can access the account and make payments to accounts themselves. The cybercrimal might also ask the victim to download screen sharing software so they can view or control the victim’s computer. This can make it easier to take control of the account. Its important to remember that often these institutions already have your phone number in their records, so, if you get an email from them asking for your phone number, it probably isn't legitimate.
Tech Support Fraud
Tech support scammers pretend to be a computer technician from a well-known company. They call their victim to make a report of suspicious activity on the victim’s account and ask them to confirm their account details. During the call they ask for the victims email address, telling the victim, they will receive an email with a link to download the software to avoid their account being compromised, but the victim is unknowingly installing malware on their computer. The second common tactic tech support scammers use is telling victims they’ve found a problem with their computer. Scammers then ask their victims to give them remote access to their computer and pretend to run a diagnostic test. Then, they try to make the victim pay to fix a problem that doesn’t exist.
Tax Scam
Tax scams are a rewarding way for attackers to gather financial information from unsuspecting victims. Tax scams generally involve a prerecorded voice message explaining an issue with the victims tax return. This is followed by a warning that if you fail to call back, a warrant will be issued for your arrest. When the victim calls back the scammer, they are urged to share finanincial information. Alternatively the victim might be told to follow instructions to click on a link they have sent to the victim via email or text message. Threatening to issue an arrest warrent if victims do not comply is a good example of how cybercriminals appeal to their victims through fear tactics.

How to reduce the risk of vishing attacks
It's important that individuals and businesses know how to recognise signs of vishing and reduce the risk of these types of attacks. Here are some things to remember when dealing with a potential vishing attack:
-
Never provide personal information over the phone
-
Pay attention to the language being used by the caller. Be wary of any threats being made or urgent requests of any kind
-
Always ask questions. Ask the caller for proof when they are trying to give you a free prize or sell something. If the caller refuses to verify their identity, hang up
-
Do not respond to emails or messages that ask for your phone number, this is usually the first step in a targeted vishing attack
What is smishing
Smishing is when cybercriminals try to trick you into sharing personal information over a text message. Smishing has become increasingly popular because people are more likely to trust a message that comes in through a messaging app on their phone over a message delivered via email. Although most of us don’t equate phishing scams with text messages, it’s become increasingly easy for cybercriminals to find phone numbers using online directories and apps that generate numbers.
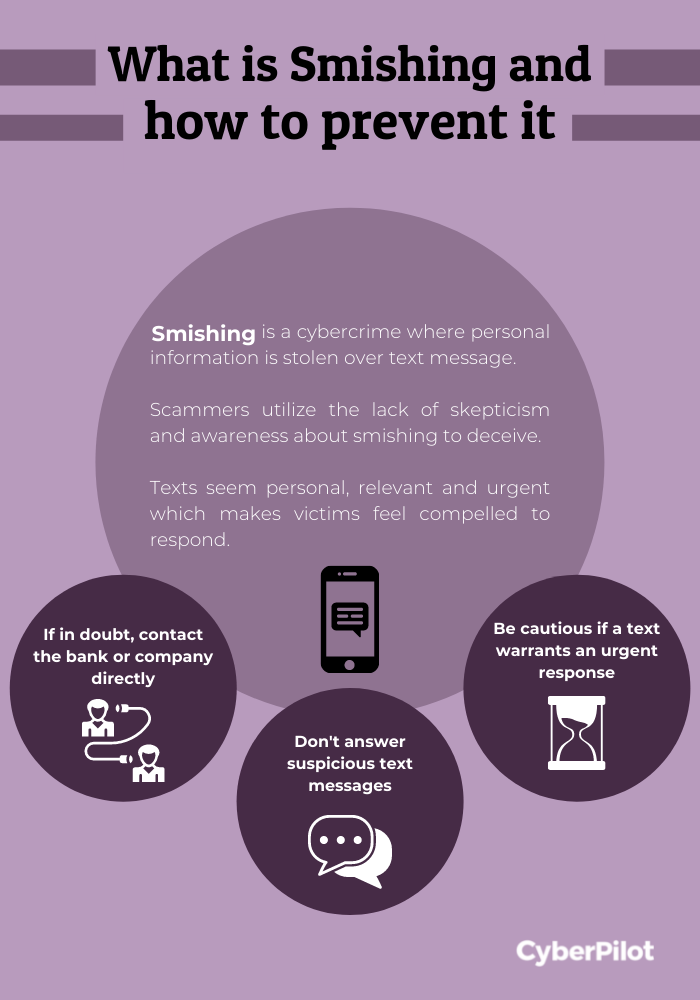
How does smishing work?
Cybercriminals take on an identity that victims trust to deceive them and to lower their skepticism. This allows cybercriminals to manipulate their victims’ decision making. Cybercriminals use situations that could be relevant to the victim, and this is normally done through making the message feel personal. Cybercriminals aim to heighten the victims’ emotions to create urgency which leaves little room for critical thinking in the situation. Through trust, relevancy, and emotional appeal, attackers create situations in which their victims feel compelled to respond.
Examples of smishing attacks
There are several different types of smishing attacks. Here are some of the most common types that you should be aware of.
Unusual activity scam
Cybercriminals impersonate legitimate organizations to trick people into clicking on suspicious links which could give cybercriminals access to your device, personal and financial information. Companies now send notifications to their customers if their account was accessed from a different device or location to enhance user security. Cybercriminals also copy the technique and send alerts with suspicious links to the victim, so they verify where the access came from. When victims receive a text message stating “suspicious activity on your account” alarm bells must ring and therefore this scam works so well for cybercriminals as victims are faced with urgency, panic and confusion, which is a recipe for disaster.
Gift card scams
Gift card scams rely on impersonation and social engineering tactics to engage with victims to ask them to purchase gift cards. Attackers often impersonate the victims’ employees or their boss as part of the scam. They make up a story about needing your help with something, an office surprise party, a company event, even a simple errand. Whatever the reason, they’ll ask you to help by paying them with gift cards, promising to pay you back later. But once you hand over the gift card number and PIN, the money is gone. These attacks work because they are a simple and quick way to get money from their targeted victims, especially when the text message is impersonating someone in the organization.
How to reduce the risk of smishing attacks
You can take some steps to ensure that you do not fall victim to smishing. The attacks can only cause damage if you respond or engage in some way, and a text message alone will not cause any harm if no action is taken. Below are a few things that you should keep in mind when you suspect a smishing attack.
-
Do not respond to the text message. Attackers depend on your curiosity over the situation but you can refuse to engage.
-
Slow down if a message is urgent and proceed with caution. A text message that warrants an urgent response or has a time limit can be a sign of possible smishing.
-
If you are doubtful about a text message, call your bank or the company directly.
-
Check the phone number. Odd-looking phone numbers, such as 4-digit ones, can be a sign of possible smashing.
 What to do if you become a victim of smishing
What to do if you become a victim of smishing
In the case where you have already fallen victim to a smishing attack, it is important to have a plan in place. To limit the damage of the attack, make sure to:
-
Change all passwords and account PINs where possible
-
Monitor your finances, credit, and online accounts for strange login locations and other activities
Building organisational awareness
It's important to train your employees to spot the signs of vishing and smishing as a first step to reducing the risk of these types of attacks. To do this, you must build a culture of awareness within your organisation. This can be achieved using our cybersecurity awareness posters, proving phishing training and awareness training courses to employees.

