Phishing is becoming a bigger and bigger threat and comes in various shapes and sizes. Whale Phishing is one of those shapes and it’s a doozy. Many companies have taken the bait and fallen victim for whale phishing. It’s important to be aware of the tactics phishermen are using to get you and your colleagues to take the bait. In this blogpost I will guide you through what whale phishing is and what measures you can take to avoid any of your employees getting caught by the phisherman.
What is whale phishing?
Whale phishing is a type of spear phishing that targets senior executives and CEOs of companies. Whale phishing shouldn’t be confused with CEO-fraud, in which cybercriminals impersonate the CEO of a company to trick an employee into transferring confidential information or money.
There are a few different ways that whale phishing takes place, I will briefly discuss some common tactics used by cybercriminals.
One of the ways CEOs might experience whale phishing is through cybercriminals sending an e-mail requesting payment, pretending to be a client of the company.
Cybercriminals may also falsely present themselves as being an employee of a company and target the CEO by sending a personalized email. All this takes is a quick google search to find relevant information about the company and CEO.
Cybercriminals often send an e-mail or a text message urging the targeted CEO to click on a virus disguised as a link. Upon clicking the link, it allows malware to install on the device giving cybercriminals access to the company’s private data.
How is whale phishing different from phishing?
The difference between whale phishing and phishing is that phishing attacks are targeted towards non-specific individuals and are carried out by sending mass e-mails. On the other hand, whale phishing is done more precisely and is targeted at individuals such as CEOs, executives and employees in higher positions in the company. In other words, phishing focuses on the quantity of attacks whereas whale phishing is all about quality as it takes a great deal of work for attacks to be successful.
Now that’ve we’ve established what whaling is, let’s talk about the purpose of whale phishing and how attacks are carried out.

Purpose of whale phishing
The goal behind whale phishing is to convince victims to either transfer a large sum of money to the attackers or to steal confidential company data. Cybercriminals choose to target those in positions of power within a company to reach this goal as these induvial tend to have decision making power and may not need approval when making payments. Another reason for targeting such individuals is that attackers see them as those who are willing to protect the company's reputation when threatened with information that could tarnish the company image.
How whaling attacks are carried out
Cybercriminals carefully choose their high-profile target before carrying out a whaling attack, they then do in-depth research to find out about the individual, their personal life and company they work for. Cybercriminals turn to social media and other public information sources to craft personalized attacks. Once the cybercriminal has a good understanding of the target’s vulnerabilities, they finally send a personalized e-mail to the target requesting a large amount of money.
How to spot whaling – common indicators
It's important for everyone to look out for common signs of phishing emails, but leadership especially need to be on alert for potential whaling emails. Here are a few things to look out for in an email that could indicate it being malicious:
-
Suspicious looking or misspelled URLs
-
Corporate looking e-mails that don’t carry your company’s domain – Gmail, outlook or other public email addresses
-
A sense of urgency or fear in the message
-
Requests to verify personal information – “can you please confirm your bank account number?”
-
Spelling and grammar mistakes
Example of whale phishing
In this section I will show you an example of what a whale phishing e-mail looks like. I’ll also guide you through some of the typical indicators of a whale phishing e-mail.
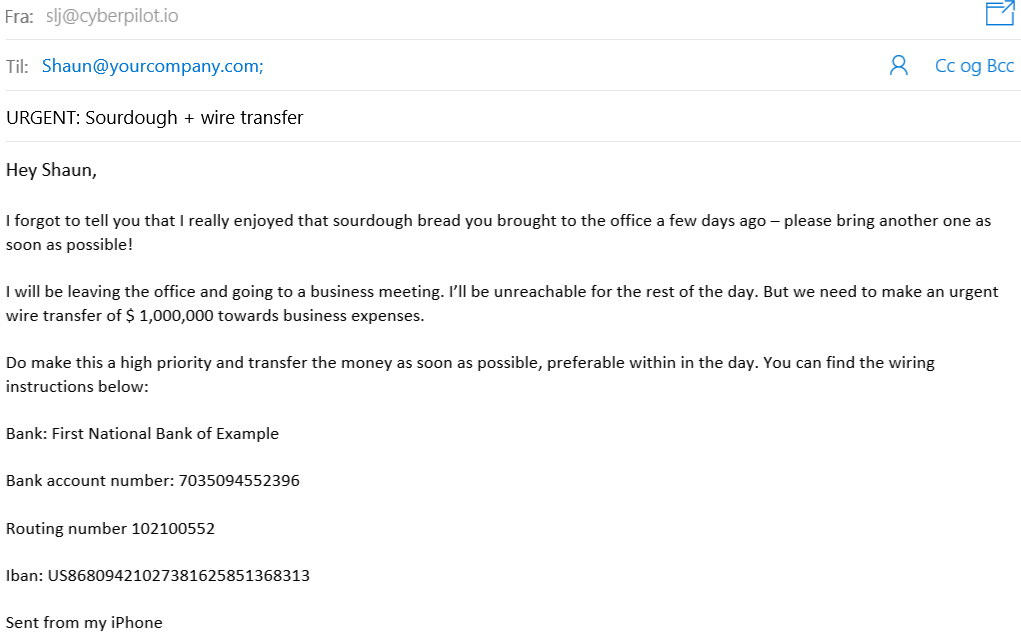
There are several indicators of whale-phishing in this email. Let’s walk through them together.
The first sign we can see is that the bosses e-mail address doesn’t match the company’s e-mail domain, as you can see the word company is misspelled. Another sign is the sense of urgency in the email as the attacker states the money must be wired before the day is over. The attacker appears to use sensitive information that makes the email seem legit, this is a sign to look out for.
The attacker personalizes the email by using information about the victim. The comment about the homemade sourdough bread is made to instantly gain the victim's trust. Shaun may have made a post on social media about bringing bread to the office including pictures of him and the boss
This is a clear example of how cybercriminals use information found on social media to make their phishing e-mails look more believable.
Whale attack consequences
Whaling attacks show that anyone can be targeted by cybercriminals and fall for phishing emails. The consequences of falling victim to a whale attack are like any other type of phishing attack, but the scale may be larger since CEOs and senior leaders often have more access to data and money. Whale phishing also has devastating consequences on organizations of all sizes as they target sensitive information as well as financial information.
Financial loss
If a person in your company takes the bait it could result in them sending a huge amount of money to the cybercriminals. Additionally, there’s the cost of investigating the breach and compensating potential customers. Ubiquiti Networks lost a staggering $46.7 million in a whaling attack, where cybercriminals targeted at top executives by impersonating a legitimate business message.
Loss of personal data
Cybercriminals may be able to obtain personal data because of the whaling attack. While financial loss might be something that your company is able to recover from, it’s more difficult to make up for the loss of people’s personal data. Snapchat fell victim to a whaling attack in 2016, where a worker transferred current and former employee's personal data to a cybercriminal who posed as the head of the company.
Reputational harm
Loss of personal data or financial loss can be extremely embarrassing for the individual who fell victim to a whaling attack. The consequences of a whaling attack could also result in a lack of trust in your company from customers. They might take their business elsewhere, especially if the whaling attack results in loss of personal data. An Australian hedge fund, Levitas Capital got duped in 2020 by a fake zoom link containing malware in an e-mail. The attack almost caused a loss of $ 8.7 million, but ultimately the cybercriminal only got away with $800.000. What Levitas Capital didn’t lose in millions they lost in reputational damage though, causing them to lose their largest client and causing the hedge fund to collapse.
Cultures consequences
If a CEO does take the bait and falls for a whaling e-mail it could give employees the impression that the company doesn’t take cybersecurity seriously. Also depending on the actions taken, perhaps the employees may get the sense that:
-
It doesn't really matter that much if you fall for a phishing email because the CEO did it and nothing happened to him or her.
-
The CEO was seriously reprimanded and now employees might be afraid to report that they accidentally clicked a malicious link in an e-mail.
How your company responds to a whaling attack has an impact on how your employees feel about data security measures. It’s therefore important to focus on your company’s culture and how your organization handles cybersecurity. Culture is important, so we've created a guide to help you create a strong cybersecurity culture in your organization.
How your company can defend itself
As written in this blogpost, a successful whaling attack could cost your company a lot of money and losing the trust of your customers. Defending yourself against whale phishing and all types of phishing should be a priority in your company. So here are some initiatives that your company can take to defend itself.
Educate your employees
A great way to defend your organization from phishing attacks is to instill a good cyber security culture in your company. Not only the those in senior positions should be educated about cybersecurity but everyone in the organization should be made aware of the dangers of phishing. Everyone in the organization should know who to contact in case of suspicious e-mails.
Implement phishing training
It’s important that your team is aware of suspicious e-mails and links, so that they don’t fall victim or provide sensitive information such as bank information, passwords, and usernames to cybercriminals. One way to train your team is by making them aware of what whale phishing is using CyberPilot’s Phishing-training.
Use appropriate privacy settings online.
You could educate your employees about social media. Executives and higher-ups can limit access to their information by setting privacy restrictions on their SoMe accounts. Setting privacy restrictions can prevent cybercriminals from exploiting that information.
Company culture
Your company’s culture is an integral part of your defense against cybercriminals. Awareness-training is just a part of the puzzle, but it’s also about creating an environment where employees are not afraid of making or reporting mistakes.
You should educate your whole team, not just the higher ups in how to identify these types of attacks. It’s about creating a positive cybersecurity culture in your company that everyone can benefit from. Recognizing phishing attempts is crucial for a company’s security. All it takes is one wrong click.

