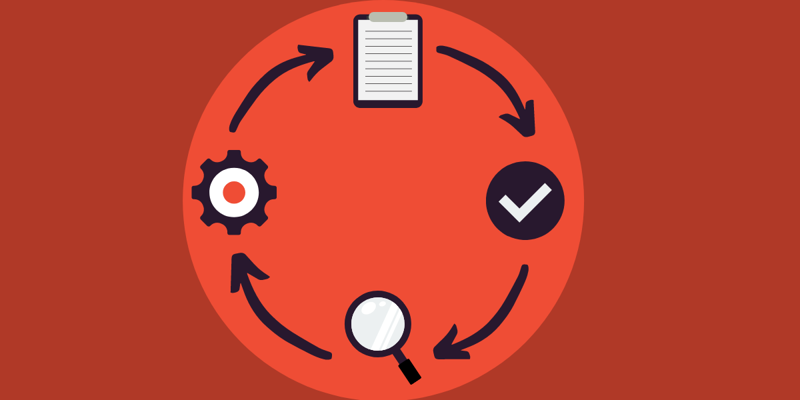
It has become common knowledge that organisations need to have good information and cyber security. Otherwise, there could be a line of consequences, such as GDPR violations, fines and, data breaches, resulting in the loss of customer trust. But what is not often considered is whether organisations have established an effective process for the ongoing development and maintenance of their information security. Since cyber security is a dynamic process, and the threats from cybercriminals are always changing, this blog post will provide you with the Plan Do Check Act cycle (PDCA) for information security and help you establish effective information security.
Short Summary:
- The PDCA cycle provides a framework for organizations to continually strengthen their information security.
- It has four stages: plan, do check, and act. We walk you through each step with an example.
- You can use the PDCA to support compliance with different security frameworks and policies, such as ISO 27001, because many of them require continuous security improvement.
Listen to our podcast about Plan-Do-Check-Act
Don't want to read? Then listen to our podcast episode, where Anders and Rasmus goes through the cycle.
What is the Plan Do Check Act model (PDCA)?
The Plan Do Check Act cycle is a model that your organisation can use for improving a continuous process. When following the cycle, the idea is to avoid making repetitive mistakes. The process is iterative, a common approach within agile management and something that is also known in fields such as Design Thinking. While the model is simple, the best result is obtained when working with the model with a long-term perspective, which will require commitment from your organisation’s management.
Description using a PDCA example
At CyberPilot, we believe that having a continual awareness program for staff is one of the strongest defences in your organisation’s information security. To provide an example of how the PDCA can be used, let’s use this Plan Do Check Act example: imagine that your organisation has just decided to implement an awareness training program.
Plan
In this stage of the PDCA, you will be identifying a problem to solve or a goal to achieve. To track the goals and targets, you must identify all the relevant Key Performance Indicators (KPIs).
Before moving on to the next stage, make sure that everybody on your team can answer the following questions:
-
What is the main problem we will be solving?
-
What resources are needed?
-
What will make the plan successful?
In our PDCA example, the overall goal could be to create awareness among the team about information security. One target could be that the majority of the team completes all training courses. A KPI can therefore be the number of courses completed. It could also be that the team enjoys the training, which would probably need a more qualitative method to check.
Do
The next step of the Plan Do Check Act cycle requires that you execute the plan. However, you should also be alert and anticipate some unpredictable problems that could occur. If the plan consists of big organisational changes, it could be wise to first test the plan on a small scale to avoid disruption. It is also important that you remember to track your KPIs.
Here, the awareness courses are rolled out to your employees in the order and pace that you determined in the planning stage. Make sure to retain the relevant data of how many employees are completing the courses.
Check
The next part of the PDCA is the check stage. By collecting and analysing the KPIs and the data, it will be clear if the initiatives have had the desired effect or if there are adjustments that need to be made. This is done by comparing the result to the expected outcome that was decided in the Plan. This is a vital part of the cycle.
In the example, the management in your organisation can analyse the result of the KPI on how many courses have been completed per employee. They can also consider looking at the number of security breaches in the organisation after the courses were rolled out and compare the number to how many you had before the initiative started. You could also talk with colleagues about what they actually think of the training. All of these checking methods help you reflect on and evaluate the plan.
Act
With the takeaways from the Do and Check steps, the processes will now be improved. In this stage of the PDCA, you will respond to the results and optimise the processes. You will then have to adjust the KPIs accordingly and return to the Plan stage. By repeating the cycle, your organisation will experience constant improvement.
Returning to the example, if the data shows that nobody on the team is completing the courses and the overall attitude has not changed, the management should find the underlying reason for this. Do the employees not have time? Do they think it is unnecessary to do the training? What is the root cause? When you figure this out, you should go to the Plan stage and see how you can make the training better and more relevant to their employees. If they, e.g., think the training is unnecessary and stupid, then maybe what is needed is communication about the importance of information security.
Information security is an ongoing process
The Plan Do Check Act cycle can be used at all organisational levels and for all types of processes. However, we believe that the model is especially useful when it comes to cyber security. An organisation will never be 100% secure or un-hackable. Cyber security is about reducing the likelihood of being hacked. Measures to improve cyber security are under constant development, but so are the cybercriminals’ efforts. Hackers have always tried to find new methods to get what they want. To illustrate this, just consider how many different ways cyber criminals can phish us: there’s regular phishing, pharming, vishing, smishing, whaling, barrel phishing, and spear phishing, just to name a few. For this reason, every organisation should use the Plan Do Check Act model when it comes to maintaining information security.
Cybersecurity frameworks also require consistent security work
Furthermore, the cycle is a part of the ISO 27001 standard, which is an international standard on how to manage information security. The standard has a requirement that your organisation uses a method for continuous improvement in your information security work. This blog post will not go into depth on the ISO standards, but achieving the ISO 27001 comes with multiple benefits, such as signalling to your clients and the public that you are committed to managing the information security in your company. Additionally, making security improvements through staff awareness training gets you closer to compliance with several other cyber security frameworks, including the GDPR.
What gets measured gets managed
Many organisations have done a good job when it comes to buying the technical parts of maintaining information security, such as antivirus software, SEIM and log management systems, firewalls, and spam filters. However, before you purchased the antivirus program, did you actually know why you bought it and what purpose the program would fulfil? Were the answers based on a risk assessment? Did the management in your organisation agree on how to measure the success of the antivirus program?
If your organisation struggles when trying to answer these types of questions, it will also be difficult to assess the value of the initiative. This means that you will not know whether it is worth pursuing.
Your organisation needs to have measures in place to be able to assess the effectiveness of the cyber security programs that you have invested in - measures such as KPIs. However, a KPI will only be efficient if you act when you notice that something is not living up to the intended plan. As shown with the PDCA example, the PDCA is a helpful tool to periodically check up on your KPIs.
Remember to customise security solutions to your organisation
Additionally, there are no ‘one-size-fits-all’ solutions in information security. A large airport has different needs compared to a small retail store. When determining which practices, controls, and programs you should invest in, the decisions should always be based on your organisation’s own situation.
The Plan Do Check Act model is a useful tool that you can use to set IT security goals and regularly evaluate your progress. You could even use the PDCA cycle to work towards goals laid out in your IT security policy. IT security is a continuous process that both the IT team and employees have to contribute to. Using a model like the PDCA cycle can help you ensure that you keep making progress toward your IT security goals.
People also asked
What is PDCA and how does it work?
PDCA stands for Plan-Do-Check-Act. It is a continuous improvement methodology used in quality management to achieve better results by planning and implementing changes, checking their effectiveness, and acting on feedback to make further improvements.
What does PDCA stand for?
PDCA stands for Plan-Do-Check-Act. It is a four-stage iterative management method used to improve processes and achieve continual improvement. The cycle involves planning a change, executing it, checking the results, and then acting on the feedback received to make further improvements in the next cycle.
When should PDCA cycle be used?
The Plan-Do-Check-Act (PDCA) cycle is used for continuous improvement of processes, products, and services. It can be applied to any situation where improvement is desired, including quality management, project management, and risk management. The cycle helps organisations identify problems, implement solutions, and monitor outcomes to achieve better results.