Do you learn anything from sending thousands of phishing emails? YES, you do, and we want to share it with you.
All our learnings can help you to get stronger security for your company.
Our data shows when, what, and how companies fall for phishing scams, and we share it all. For example, you can read about how your users are most likely to fall for scams that include rewards and urgency. Curious? Let's go.
Intro
We've sent a bunch of phishing emails, at different times of the day, with different content and various techniques to get people to click and submit data.
All of this data collected and structured gives us a bunch of learnings.
Now, we want to share them with you, so you can learn from them.
Before diving in, we want to make two definitions clear:
Click Rate= people clicked the link in the phishing mail
Data Submit Rate = people tried to login by typing in their username and password on the following page after they've clicked the link in the email.
With that in mind, we are ready to dive in. Here's a table of contents of all the treats you are in for.
Table of Content
What is phishing?
Phishing is malicious emails trying to get you to click links, submit data, or download malware.
Criminals use them to steal data or hack companies. They often pretend to be from someone you know or trustworthy companies.
The consequences of phishing attacks
The consequences of a phishing attack can be enormous. Therefore, it's important that your company does everything it can to avoid them.
This can be everything from technical setups to training your employees.
Here are some examples of consequences:

Now we know what phishing is and what the consequences of attacks might be.
Let's take a look at all the data.
The data behind the insights
Before going crazy with all the insights, here's what we base it on.
We've sent over 200.000 phishing emails, and all of this data comes from these emails.
The emails are sent to our customers. It's simulated phishing attacks, meaning no company has been harmed.
We send generic automated phishing emails and spear phishing attacks targeting specific companies. The overall data comes from both types of phishing attacks. We use both types because we see criminals use them as well.
In this data, we've only used classical phishing. We are not using methods such as smishing, vishing, whaling, or other kind of phishing attacks. Only "normal" phishing and spear phishing.
Types of tells and how they perform
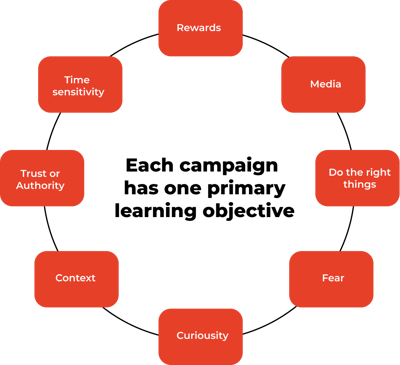
We use 8 different signs of phishing in our emails. These signs are the ones we see the most out in the real world. We train companies in spotting all of the signs.
One email can include more than one sign.
The 8 signs are:
- Rewards
- Curiosity
- Context
- Media
- Time-Sensitivity
- Do-the-right-thing
- Fear
- Trust or Authority
You can read a more thorough walkthrough right here.
We've learned from our data, that not all signs are equal.
People are having a harder time spotting some than others.
Rewards and time-sensitivity are the most difficult signs to spot
Of the 8 signs 2 of them stand out the most.
Rewards and time-sensitivity.
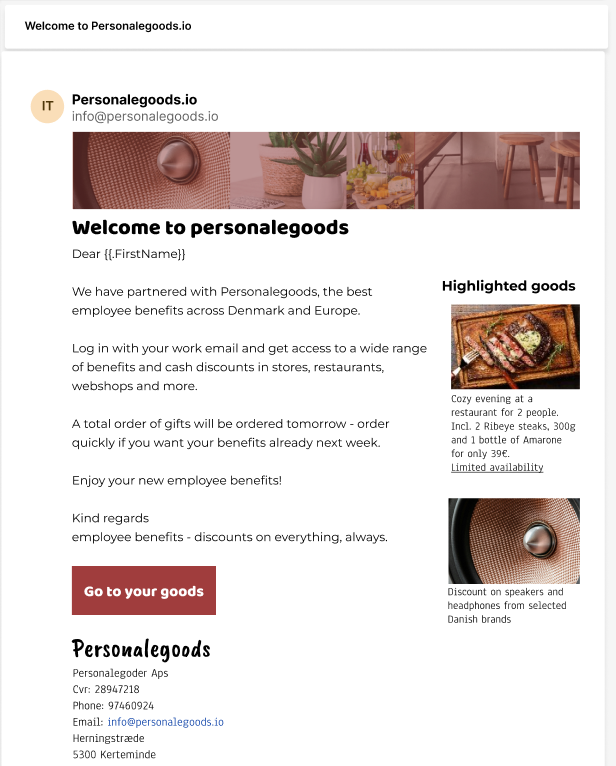
Rewards are emails where the reader gets some kind of reward for doing something. Here's an example of an email:
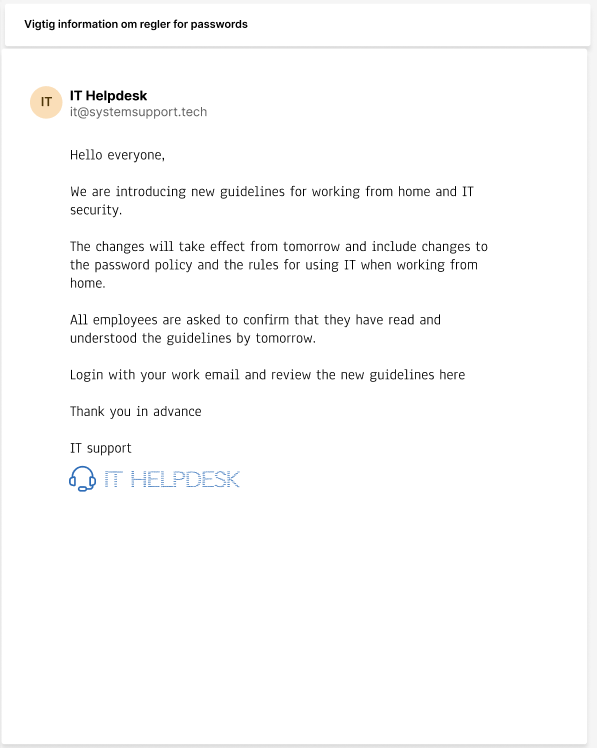
Time-sensitive emails are those where there is urgency to do something. For example, you may only have 24 hours to update your password.
These two methods are the ones where most people click the links.
Click rates:
Rewards: 16,4%
Time-sensitivity: 16,9%
If we look at the data submit rate, it turns out, that urgency is pushing people to submit - maybe because they don't stop and reconsider after clicking.
Data submit rates:
Rewards: 8,3%
Time-sensitivity: 10,8%
It shows, that we really need to train our colleagues to be aware. If something in the email indicates you get a reward, or have a sense of urgency in it - this should be a red flag.
Every single time.
The other signs also get clicks
But, unfortunately, we don't just need to teach people about rewards and time-sensitivity.
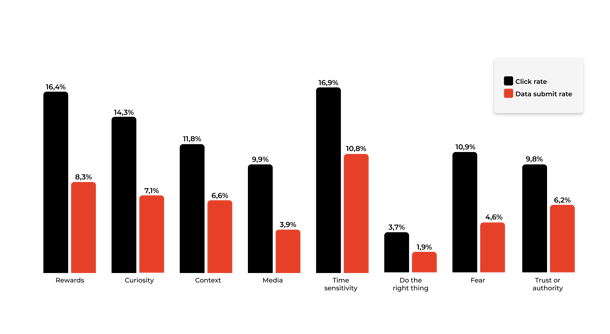
Here are the click-rates for all signs:
| Sign |
Click-rate |
| Time-sensitivty |
16,9% |
| Rewards |
16,4% |
| Curiosity |
14,3% |
| Context |
11,8% |
| Fear |
10,9% |
| Media |
9,9% |
| Trust or Authority |
9,8% |
| Do the right thing |
3,7% |
And the data submit rates:
| Sign |
Data Submit Rate |
| Time-sensitivty |
10,8% |
| Rewards |
8,3% |
| Curiosity |
7,1% |
| Context |
6,6% |
| Fear |
4,6% |
| Media |
3,9% |
| Trust or Authority |
6,2% |
| Do the right thing |
1,9% |
It's worth noticing that even though Trust and Authority is only the seventh most clicked phishing method, it's actually in fifth place when it comes to data submission rates.
A hypothesis is that because it's about trust, you are less likely to reconsider on the landing page.
All signs get clicks and submissions, and it shows that you need to train your company in all of them. You might get good at spotting one type of sign, but we see them all in real attacks. You need your employees to be aware of them.
At what time are people most likely to click
Okay, but what about time? Does the day of the week or the time of the day matter?
It looks like it. Here's what we've found
Monday and Tuesday are the worst
Most people hate on Mondays. Maybe so much that they'll rage-click phishing emails.
If we look at our data, people are most likely to click phishing links on Mondays and Tuesdays.
Monday click rate: 12,66%
Tuesday click rate: 13,43%
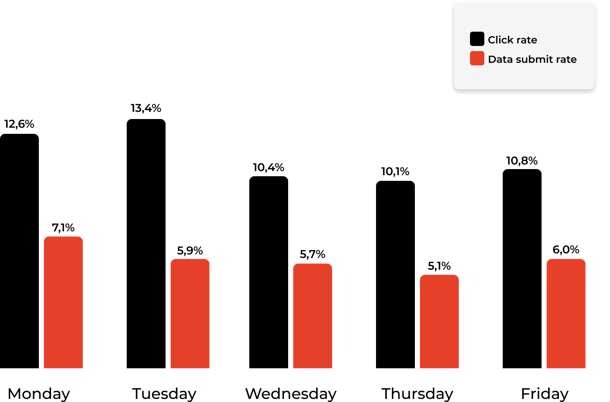
We see a drop the other days 10,8% on Fridays being the closest.
Why do people tend to click more at the beginning of the week?
We think it's because people are busiest these days. There are studies suggesting that Monday and Tuesday are people's most productive days.
So yeah, no matter why, be extra aware these days ;)
Oh, and we've also tested Saturday and Sunday.
Luckily, people chill on the weekends, and the click rates are very low here.
The time of day people click
Now, we are diving into something that surprised us.
The time of day that people seem to be most likely to click phishing emails and submit data.
We thought people were most busy in the mornings and, therefore, most likely to fall for a phishing scam. Therefore, we sent most of our emails during this time.
But our data suggests otherwise.
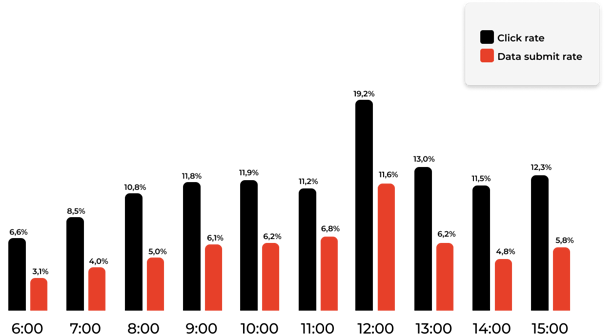
Most people click and submit data between 12.00 and 13.00, during lunchtime. Here, the click rate is 19.2%, and the submit rate is 11.6%.
We don't have any suggestions why, but the data speaks for itself. The click rate is way higher from 12-13.00 so you and your colleagues need to be extra aware at lunch time.
Spear phishing vs. Automated phishing
We differ between two kinds of emails in our phishing training
Spear and auto.
Spear phishing
We design the email specifically for the company we are targeting, using its logo and information from its website. Criminals do this when they want to target a specific person.
Here's an example: if a company writes about an event or company party on their website - we might use this information to create a phishing mail about this event to get people to click.
Auto phishing
Auto phishing is "mass-sended" phishing emails.
This email could be sent to every company and person in the world. We don't use any information about the victim but only use psychological tricks and tactics to get them to click
This is the kind of email most companies face every single week.
The performance gap is as obvious as a cat in a dog show
The question is:
Are your company more likely to fall for a spear phishing attack than an auto phishing attack?
The short answer is YES.
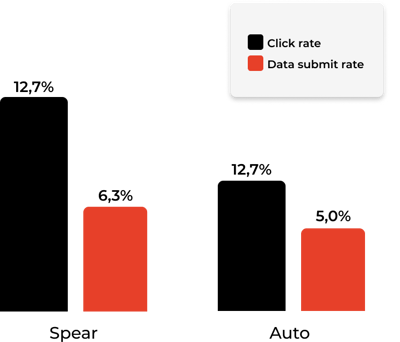
We see a click rate above 12,76% throughout our campaigns in our spear phishing attacks.
Our auto phishing is "only" around 7,8%.
The click rate is 50% higher in spear phishing attacks.
It's not as obvious with the data submit rate
The difference in the data submit rate is not as big. Here, we see a submit rate of 6,32% in spear phishing and 5,06% in auto.
This suggests that people stop to think when they hit the landing page, and maybe it's because we have a harder time faking the landing page in a trustworthy way, as we don't know how it would look like in the companies we are trying to hit. It's harder to spear phish a landing page than an email.
The good news: People learn to spot phishing
All of these stats can be a bit of a devastating read.
But don't worry. There's a light in the dark.
We see that people can learn to spot those phishy bastards.
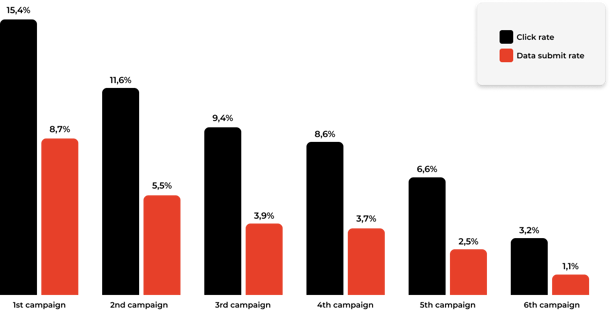
We see that our customers become better and better at spotting phishing emails. As a result, fewer employees click and submit data for each campaign they receive.
This is even the fact if we send spear phishing.
It shows that it's important to train your employees to look for the signs of phishing emails. If this becomes a habit, they can spot them, warn their colleagues, and report the emails to IT.
Remember, that if you want to test your company and compare your performance to all over the above stats. You can read more on our phishing training page on how to get started.

