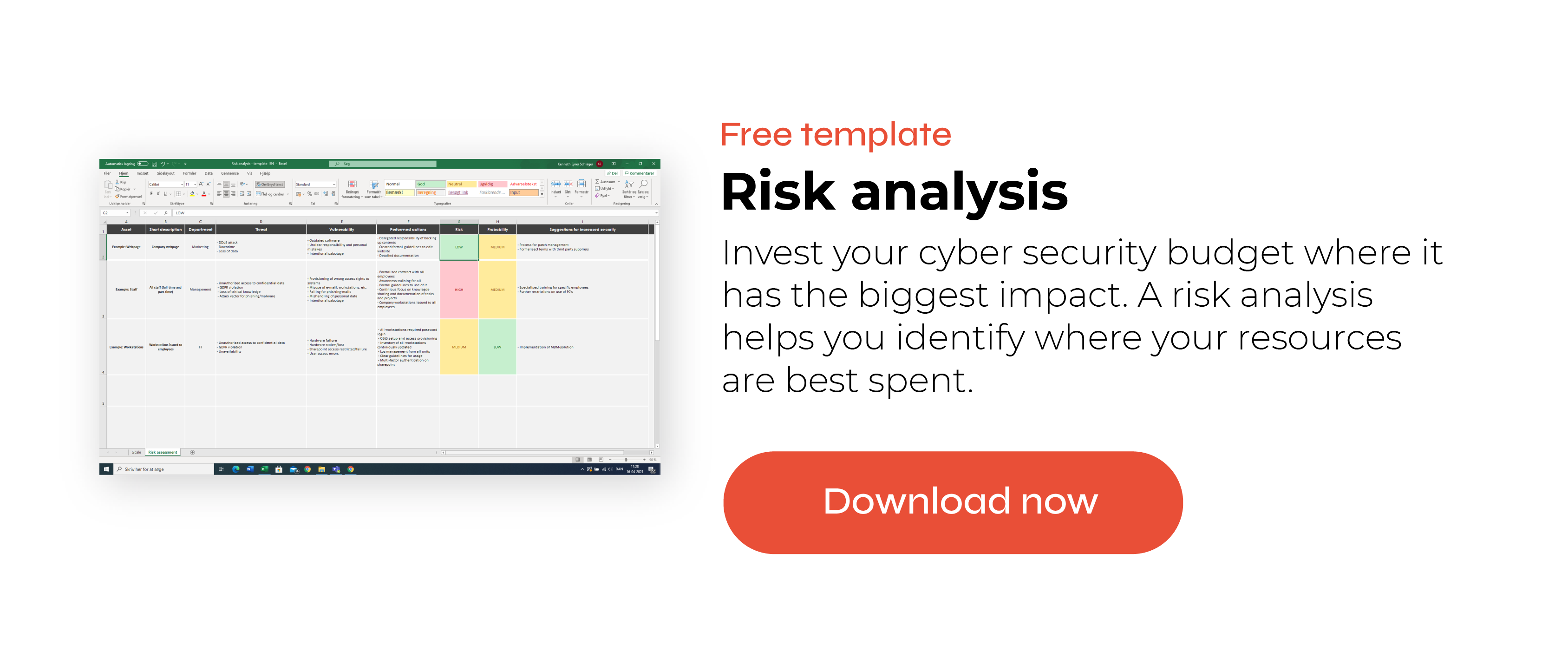
How To Make an Acceptable Use Policy – Example with Free Template
Having an Acceptable Use Policy (AUP) can help strengthen the information security in your organisation. In addition to promoting a strong information security culture, it also ensures that the entire organisation is on the same page and knows how they should handle their digital activities. The goal is for everybody in the organisation to feel confident in knowing what they can and cannot do.
In this blog post, we will guide you through an Acceptable Use Policy example by using our AUP template. We will also discuss what to consider when you create these guidelines for your organisation.
Table of Contents
- Information Security Policy vs. Acceptable Use Policy
- How to use the AUP template
- Purpose statement
- Guidelines and principles:
1. Confidentiality
2. Access codes (passwords and PIN codes)
3. Physical security
4. Handling equipment and files outside of premises
5. Equipment and software
6. User credentials
7. Digital activity
8. Security monitoring and logging
9. Handling of personal data
10. Reporting security incidents
-
The guidelines in our Acceptable Use Policy Example are a first step to reinforcing good habits
-
An AUP contributes towards a strong foundation for your cyber security culture
When working with cyber security, it can be very useful to have both an IT security policy and an Acceptable Use Policy. Both documents work together to provide a clear set of expectations, which will strengthen your security by outlining IT security goals, responsibilities, and requirements for employees. You can use our templates for both policies as guides that can help you get started.
The purpose of an Information Security Policy is to provide a general set of objectives for the organisation to aim for. Additionally, it emphasises that all staff are responsible for maintaining the organisation’s IT security. The policy is a small document with only a few pages, and it serves as a management memo with ambitions for the organisation’s information security measures. The link above will take you to a free template and tutorial for making your own information security policy.
The Acceptable Use Policy (AUP) is more extensive and includes rules and guidelines, which the entire organisation must follow. While the Information Security Policy is general and strategic, the Acceptable Use Policy for security is concrete and actionable.
While the Information Security Policy provides strategic objectives, the Acceptable Use Policy defines specific rules to follow. Basically, it includes what should be incorporated into one’s daily routine while working. For example, it can include guidelines about the length of passwords, safe use of Wi-Fi, clean desks, sending personal data over email, or private use of company equipment, like laptops and smartphones.
The purpose of the AUP is to create the field for the organisation to play on. The AUP should provide clarity to all staff members, so the guidelines should be easy for everyone to understand and follow.
You’ll know that your AUP is successful when nobody in your organisation has to debate whether they are breaking the rules. The guidelines should be really clear in setting out expectations, so that everyone can easily navigate through their daily work life in a secure way. Additionally, the document should be concise, as too many rules can be overwhelming and might ultimately lead to worse information security.
Since every organisation is different, we recommend that our AUP template serves as an example, giving you inspiration for your own policy. Your organisation has its own needs and context that might make only some of the rules relevant. So, we recommend taking what is relevant to you, adding your own guidelines, and removing the rest.
The AUP template contains guidelines on the following topics:
-
Purpose statement
-
Confidentiality
-
Access codes (passwords and PIN codes)
-
Physical security
-
Handling of equipment and documents outside of premises
-
Equipment and software
-
User credentials
-
Digital activity
-
Security monitoring and logging
-
Handling of personal data
-
Reporting security incidents
Additionally, the AUP template contains two main sections:
- Purpose statement
- Guidelines and principles
Guidelines and principles cover 10 focus areas for the rules in your organisation. We will go over each point below, after we discuss the purpose statement.
First, we provide a purpose statement to set the tone and communicate the objectives of the Acceptable Use Policy. Generally, this should state that the document is a set of guidelines that all staff in the organisation are expected to follow. Here is an example:
“X (name of organisation) focuses on ensuring the availability, confidentiality, and integrity of its systems and data. All staff must act in a responsible, ethical, and legal manner. All X staff, consultants, and temporary staff are required to manage knowledge with care and discretion, whether written, electronic, or verbal.
Therefore, the handling of data must be per X’s information security policy and follow the listed guidelines and principles. To ensure this, the staff of X are continuously trained and made aware of topics within cybersecurity and the GDPR with continuous training.”
In short, the purpose statement lays down the basic rules for the use of IT in your organisation. It should explicitly state the expectations related to your staff’s continuous training and awareness.
The guidelines and principles point out specific rules to follow when using IT systems in your organisation. Here, we have added 10 points you can include with some guiding text.
Confidentially is normally included in employment or project contracts, but it is still useful to state it in the guidelines to emphasise its importance. It states that the organisation expects confidentiality from its employees when it comes to confidential information, e.g., customer information. We give an example here:
“You must handle all of X’s information with discretion and care. Under no circumstances should you access or use information, systems, or networks that are not necessary for your job. Do not share confidential information with colleagues, consultants, or temporary staff who do not have a job-specific need for this information. You may not share confidential information with third parties unless it has a clear business purpose. When working with external parties, they must have signed a declaration of confidentiality."
In this section, the organisation can set requirements for the users’ access codes. For example, you can state requirements for the length, use of digits, or characters. You can also use this section to discourage staff from reusing passwords. We give an example here:
“All passwords and PIN codes are personal. To create a strong password, we recommend a long password of at least 12 characters, using both uppercase and lowercase letters, numbers, and special digits. When leaving your workstation, you must log off or lock the machine. Never leave passwords written on bulletin boards, paper, or stored on hard disk/email.”
We have also written a blog post with tips on how to make strong passwords that your team can remember, in case that it useful.
The physical security section deals with how to handle information stored on physical equipment. It also provides some good practices and pointers on what to be aware of in physical settings. We provide an example here:
“Please ensure that your desk is organised and that there are no important documents in plain sight when you are not using them. Confidential information must be placed in locked drawers, cupboards, or the like to avoid unauthorised access. Additionally, be aware of the visibility of your PC screen – you should not have confidential and sensitive data open when unauthorised persons are behind you, allowing them to observe your activities over your shoulder.”
This section provides recommendations on how employees should handle equipment and files when they are outside of your organisation’s premises, e.g., when working remotely.
Here, you can describe how expectations may differ based on whether the employee is physically in the office. This section mainly focuses on securing your organisation’s IT equipment. We provide an example here:
“If you bring IT equipment outside of X’s premises, it must be secured with a pin or password that ensures a sufficient amount of security against access by unauthorised persons. When flying, mobile equipment (I.e., laptop and mobile device) and documents must always be carried as hand luggage."
Nowadays, we use cloud services and software, which can be quickly accessed and downloaded from the internet. Therefore, it is essential to make some general rules on what types of services may be used and downloaded, as it can be incredibly difficult to control and keep track of your team’s activities. We give an example here:
“All IT systems, equipment, or memory storage devices must be approved by X and follow company standards as issued. Never connect unauthorised equipment to workstations or networks. This also applies to USB drives and smartphones. Additionally, you may only install or download programs if you have been permitted to do so.
Software and equipment are the property of X and must be treated accordingly. Therefore, they must not be lent to others, including family. For data handling, you must use X’s internal file server. Use of cloud-based services such as Google Drive, Dropbox, and web-based file sharing is only allowed if receiving data from external parties. It is not permitted to upload X’s data to unauthorised services. The software must always be used according to the license terms entered by X.”
Some other ways to keep track of your team’s activities are through asset management and mobile device management.
User credentials deal with usernames and passwords that are used for logging in to the organisation’s IT systems. For example, multiple users could share user information and make use of each other’s logins. However, we recommend that you only use your own credentials, so that you do not get into trouble because of the actions of others. We give an example of the guideline here:
“User rights must be respected, therefore only use your own user credentials to log in. Never share your user information with others, including your employer. Misuse of credentials and digital activity can leave digital traces that have a negative impact on X.”
Here, you can discuss best practices and limitations for digital activity on company-owned equipment. It is important to set realistic expectations, and some of these can include what we normally consider common sense. For example, it would be outrageous to ban visiting specific public websites or checking one’s private emails, but you can limit the level of private consumption during work hours. Needless to say, illegal websites and activity should be banned. However, it is up to your organisation to specify these rules, giving your team some freedom while maintaining boundaries. We provide an example here:
“Please minimise the private use of the Internet and email on X’s equipment. For personal documents, save it locally in a folder on your computer and label it ‘Private.’ Personal data must not be sent by email. Under no circumstances, may work-related online correspondence take place through anonymised communication channels. It is strictly forbidden to use X’s email accounts, computers, tablets, and mobile phones to view pornographic, racist, extremist, or criminal content. When receiving an email, the sender’s email address must be checked before unknown links and documents are opened.”
The last section of this example can help protect your organisation from phishing attacks, which are one of the biggest security threats that companies face.
The purpose of this section is to communicate that you, as the organisation, can log and monitor your team’s digital activities for security purposes. It does not necessarily mean that the monitoring is routinely done. In this section, it’s important to also communicate that you respect your team’s privacy. By bringing potential monitoring to your staff’s attention, you can encourage them to conduct their digital activities within reason. We provide an example here:
“X respects the individual employee’s privacy and complies with local laws and regulations. However, we reserve the right to log IT use and, in special circumstances, require access to an employee’s email and files.”
Proper handling of personal data is one component of GDPR compliance. Normally, compliance with GDPR requires more elaborate processes than a set of rules in a document for IT use. However, the guidelines are still a place where employees can be made aware of some general requirements to abide by, when handling personal data. These guidelines do not say much about the processes that make your organisation GDPR compliant, but they can create awareness of the importance of handling personal data. We give an example here:
“At X, we are very careful to take good care of and protect the personal information that our customers, members, employees, and partners have entrusted us with. We work continuously to develop and implement secure processes, which must ensure the legal and secure processing of personal data.
We have established the following basic principles for the processing of personal data:
-
Employees may only access personal data that is relevant to their work and function
-
Personal data should only be shared internally if it is relevant to the recipient’s task and function. E.g., personal data from a client
-
Emails containing personal data should be deleted once the relevant data has been processed
-
Personal data must not be stored locally or in one’s inbox for longer than necessary. Instead, use one of the systems designated for this in the organisation.
-
Both physical and digital files should be periodically reviewed to ensure that they do not contain personal data that is stored longer than necessary.”
Proper handling of data is a huge part of keeping your organisation GDPR compliant, so, we’ve written a few blog posts that take a deeper look into different aspects of personal data. For example, you can read more about different types of personal data, who should have access to personal data, and how to securely destroy personal data.
The last point is to illustrate the importance of reporting security incidents. As clear communication is the only way to warn and protect everybody else of the incident, it should be required for staff to report safety incidents that they observe or are exposed to. In this section, you can provide examples of what a security incident might involve and to whom incidents should be reported. The important thing is that your team is aware of when to act and who to involve. We give an example here:
“If you suspect a security incident, you must immediately report it to your immediate manager and the IT department.”
Examples of security incidents:
- You have received a suspicious email
- Emails with personal data have been sent to the wrong recipient
- Lost IT equipment
The AUP guidelines make it possible for your team to easily check what they can and cannot do. However, it is important to point out that this effort cannot stand alone; you can’t just write down the rules and expect everyone to follow them. In addition to the policy, it’s also important for your team to receive continuous training to ensure that awareness is always present.
The Acceptable Use Policy provides a good foundation for creating a strong information security culture in your organisation. It is important that your security policy documents, including the AUP and the IT security policy, do not just lie around and collect dust. After you have made the policies, you should continuously review and update them. We recommend that you do this annually. Additionally, you should take care to actively work with the objectives and guidelines from the two policies, so that the information security culture in your organisation is reinforced.
We hope you found the template and guide useful! And if you still need to create an IT security policy to supplement your AUP, feel free to download our template for that as well.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.