The Danish Data Protection Authority has put together statistics on security breaches as part of their data and risk-based strategy. These statistics are updated monthly, to help businesses make good risk-based decisions. For evaluating your own security risks, I recommend using our risk analysis template. In this blog post I will go over what the statistics are saying right now.
Types of GDPR and security breaches reported
The Data Protection Authority put together a report based on the reports of GDPR breaches it receives. In the statistics, the Data Protection Authority has presented the types of security breaches that are most often reported to them. The 10 most common GPDPR breaches are:
- Correct information going to the wrong recipient
- Protected address exposed wrongfully after change in an IT-system
- Incorrect transfer of data in case management
- Failure to delete data when using digital tools
- Auto-complete causing emails to be sent to wrong recipients
- Loss/theft of devices with unencrypted data
- Too broad access to data on network drives, etc.
- Unauthorized access to data due to poor design, code errors and insufficient testing
- Disclosure of data stored in templates and forms
- Malicious software (ransomware) causing data loss and misuse
At first glance, none of these categories appear to have anything to do with cyber-crime/hacking, but rather seem to just be normal everyday accidents. Only 2 of the 10 most common GDPR and security breaches are due to malicious actors.
This shows the importance of training employees and creating awareness so that they can avoid making these mistakes in their work.
Security breach reports are categorised
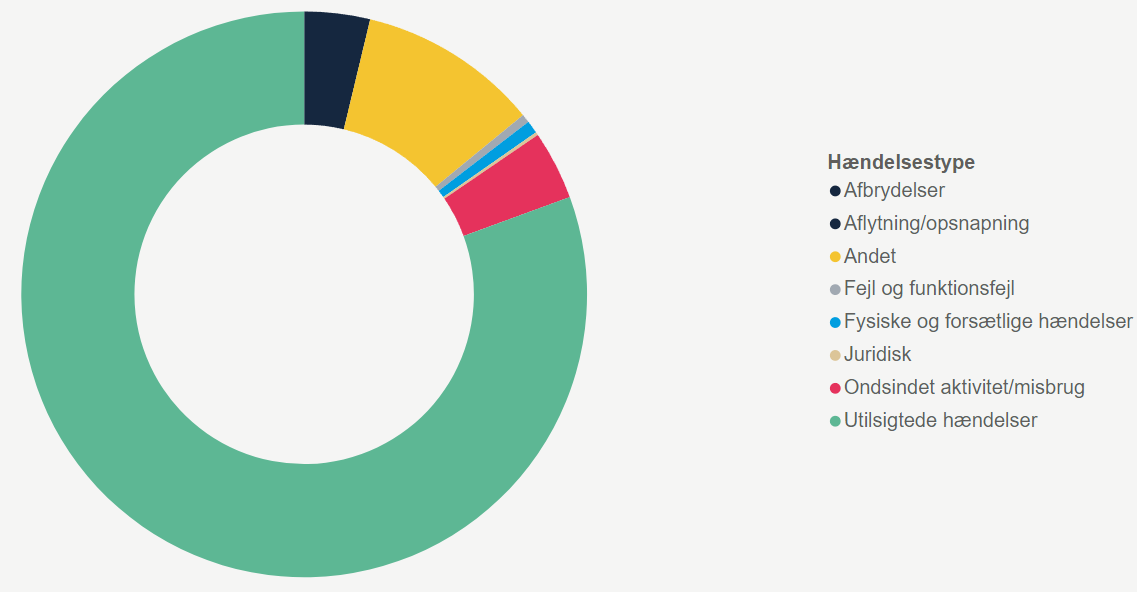
Before diving further into the ten most common GDPR breaches, let’s take a step back and consider what the statistic is actually made up of. When the Data Protection Authority receives a report of a security breach, they categorise the report based on what took place in the incident. The report can be put into one or many categories based on the incident, and there is also an “other” and "unknown" category for incidents that don’t fit into the standard categories. The categorisation looks like this:
Do you want to see what else is reported? check out the Data Protection Authority here.
The Data Protection Authority has placed 32557 breaches into the categories above.
Explanation of the different types of GDPR breaches
The data protection authority screens all of the reported breaches and categorizes them depending on what type of threat or risk which is relevant to the breach. Here is how they categorize the breaches.
Physical and intentional incidents
Personal data breaches resulting from intentional physical activities, such as threats, break-ins, theft of devices, sabotage or deliberate unauthorized sharing, disclosure or removal of data.
Unintended incident
Personal data breaches that are primarily caused by human error. E.g. lack of anonymization or pseudonymization, incorrect journaling, filing, publication of personal data, errors caused by suppliers or guests.
Accidents
Personal data breaches due to accidents such as fire, heavy rain or similar.
Errors and malfunctions
Personal data breaches caused by unintentional errors in programs or equipment, including errors in the supply of e.g. cooling or power or errors at suppliers.
Interruptions
Breaches in the availability of personal data caused by the unavailability of underlying assets, e.g. staff or internet.
Eavesdropping/interception
Breach of confidentiality of personal data due to information being intercepted, e.g. unsecure emails, unsecure internet traffic or eavesdropping.
Malcious activity/Misuse
Breaches of personal data security due to cybercrime, e.g. identity theft (including misuse of accounts for login), phishing, fraud attempts, manipulation of data with unauthorized access, targeted attacks, DDOS, exploitation of trusted rights, certificate fraud.
Legal
Personal data breaches resulting from violation of applicable regulations and breach of contracts.
Other
The incident type is selected when none of the other incident types are descriptive of the incident.
Unknown
The event type is selected when the reported breach is not classified with an event type.
The biggest issue is unintended incidents
Going back to the most common types of security breaches, the most frequent type is “unintended incidents”.
80,62% of all reports are based on unintended incidents caused by human error. It might seem like a small problem, but a whopping 26,248 out of the 32,557 reports fit in this category. It shows how easy it is to accidentally make a mistake in your everyday tasks. Maybe you added the wrong recipient to an email or gave a user too many user rights in a system. One small wrong click can cause an entire security breach.
Because of breaches like these, it is important to teach your employees to check through everything an extra time before hitting “send”, or before granting a person access to data. As easy as it seems to avoid such a mistake, it is just as easy to make that mistake.
Awareness of these simple pitfalls is important to avoid them. Technical solutions can solve many problems, but they can’t prevent a person from sending information to the wrong person.
The most common GDPR breaches are NOT caused by hacking
As mentioned, the 10 most common breaches are:
- Correct information going to the wrong recipient
- Protected address exposed wrongfully after change in an IT-system
- Incorrect transfer of data in case management
- Failure to delete data when using digital tools
- Auto-complete causing emails to be sent to wrong recipients
- Loss/theft of devices with unencrypted data
- Too broad access to data on network drives, etc.
- Unauthorized access to data due to poor design, code errors and insufficient testing
- Disclosure of data stored in templates and forms
- Malicious software (ransomware) causing data loss and misuse
Most of these breaches do not involve hacking or complicated attacks. Rather, they are caused by normal everyday situations gone wrong, through a tiny mistake and fit under the category “unintended incidents”.
Because of this, we must assume that the majority of the most common GDPR incidents happen through employees. It could be possible that an employee accidentally put personal data on a website, where everyone can access it. There are countless ways to accidentally publish data that should not have been made public.
Most security breaches happen due to human error
It is not possible to see how many percent each of the most common GDPR breaches fill in each of their respective categories – but common among all the 10 of the most commons breaches is that the mistakes will often be due to human error. It shows how breaches often depend on behaviour.
Unintended incidents make up over 80% of the reported breaches that the Date Protection Authority has received. Looking at this from a risk assessment point of view, it would make sense to look into how these GDPR breaches can be avoided. For good reasons, it is not possible to decipher what the “Other” category consists of. When it comes to the other categories, our assessment is that it is possible to significantly lower the risk of security breaches, if you teach your employees about the GDPR and make them aware of how easy it is to make and avoid these types of mistakes. You can also read our comprehensive guide on how to stay compliant with the GDPR.
These numbers highly support what we have written in our e-book (which, by the way, is free). In our e-book, we focus on how the biggest risk for security breaches lies with your employees. Training your employees is therefore a crucial cornerstone in creating a good cyber security culture in your workplace.

IT criminals only make up a small part, but the consequences are greater
Security breaches caused by criminals only make up 3,89% of the reported security breaches. That corresponds to 1268 breaches (out of 32557 total breach reports) that fit into this category, which includes:
The probability of experiencing one of these attacks is therefore not that great.
That does not mean that these types of attacks are not relevant to defend yourself against, as the consequences in these types of situations often will be great. Last year, we saw several companies lose millions due to ransomware cases, which also landed them some hefty fines due to breaking the rules of the GDPR. So even though these types of breaches do not happen that often, the consequences are great enough that you have to take them seriously. In our blog post about the cost of a data breach, you can read more about how expensive security breaches can be.
Use a risk assessment to protect yourself from potential breaches
The essence of a risk-based approach, which is recommended by officials, is that you conduct a risk assessment. This assessment will contain information about how great of a risk there is for a situation to arise, and how big the consequence for a given situation could be. Based on this you can assess where you want to use your resources. It is about avoiding spending energy on a type of incident, where the consequences are low or the probability of it happening is almost non-existent.
If ransomware was not a threat last year, it could be that the consequences are great, but the probability is so small that you will not have to focus on it. That is unfortunately not the case, as ransomware is a real risk.
Assess your own biggest security risks with the help of our risk-assessment guide and template.
IT security requires focus on behaviour and people
As mentioned earlier on, the statistics show that the majority of security breaches happen when we make mistakes in our everyday work. For example, we might accidentally send personal data to the wrong people. Heightening your focus on awareness training can therefore be a good idea, in order to boost your IT security and reduce the risk of security breaches. If you can train your employees to think twice before they click on something, then you have already gotten far.
Where technical solutions such as firewalls and anti-virus programs can help, there is also a need for aware employees when it comes to threats such as hacking, social engineering and ransomware. The Danish Data Protection Authority mentions that the majority of hacking incidents start with a simple phishing email. Therefore, awareness training and phishing training can be good tools to ensure that it will not be one of your employees who makes a mistake.
Unintended incidents are the main cause for GDPR breaches
In summary, the fact that over 80% of GDPR breaches result from unintended incidents highlights the importance of the human aspect of data protection. The fact that they’re unintentional might make it tough to do anything about them since there’s no bad intentions from your coworkers. One thing you can do to try and mitigate these incidents is by creating a general level of awareness around these issues by creating a strong security culture.
The statistics from the Data Protection Authority will continuously be updated, so we recommend that you stay up to date on the latest trends in types of security breaches.

