4 campaigns to kickstart
your phishing training
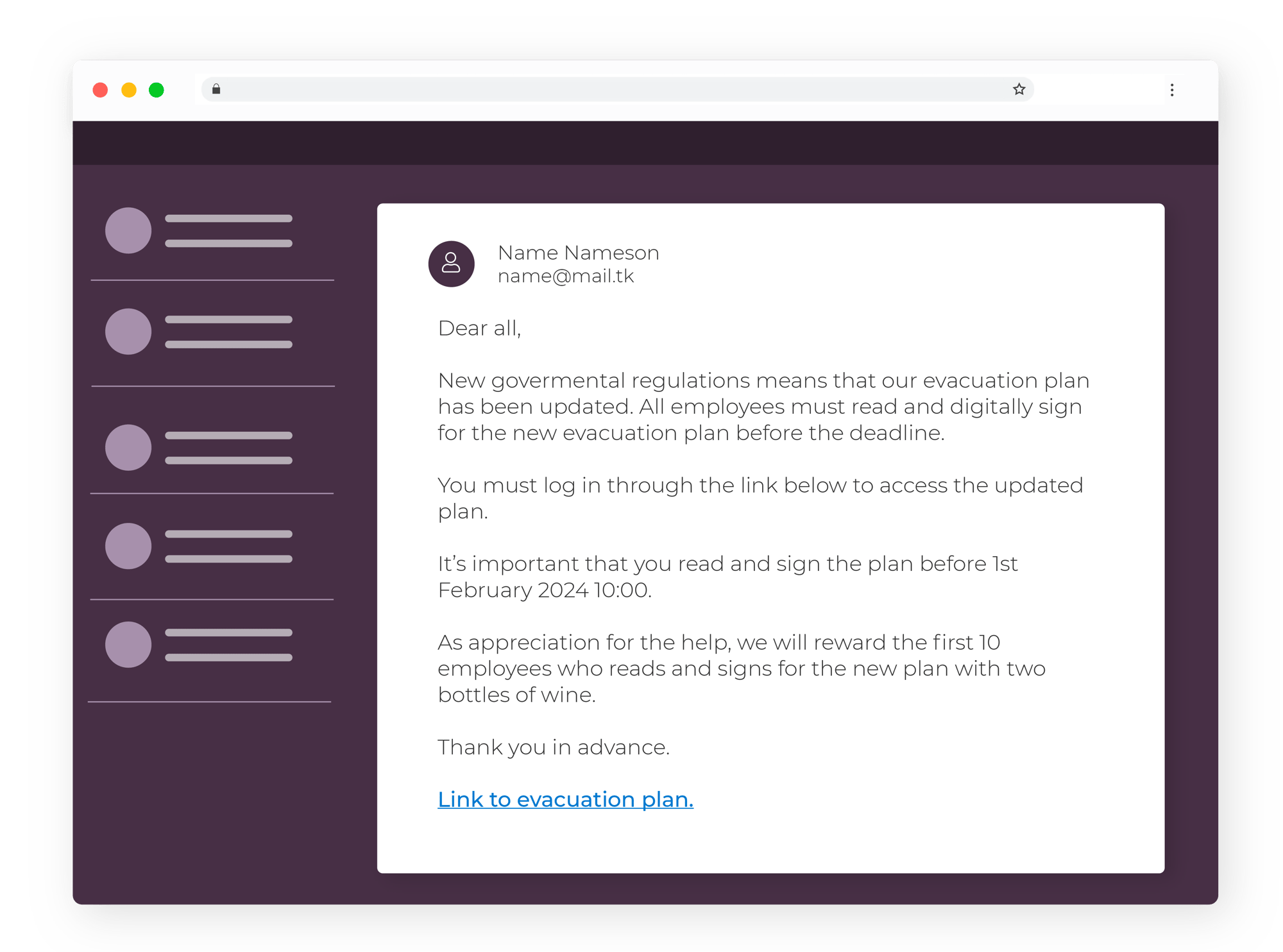
Emergency evacuation plan
This e-mail tells the reader that there is a new emergency evacuation plan that must be read by all employees. It takes advantage of the authority of the company.
Difficulty: 🐟🐟🐟🐟
Phishing giveaways:
- Unconventional request
- Changes in response policies despite no warnings
- Short deadline
- Why would you have to login to read this type of information?
- Promise of rewards
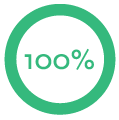
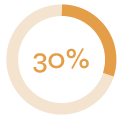
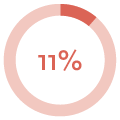
How the campaign performed:
 |
 |
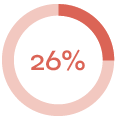 |
| E-mails sent | Links clicked | Submitted data |
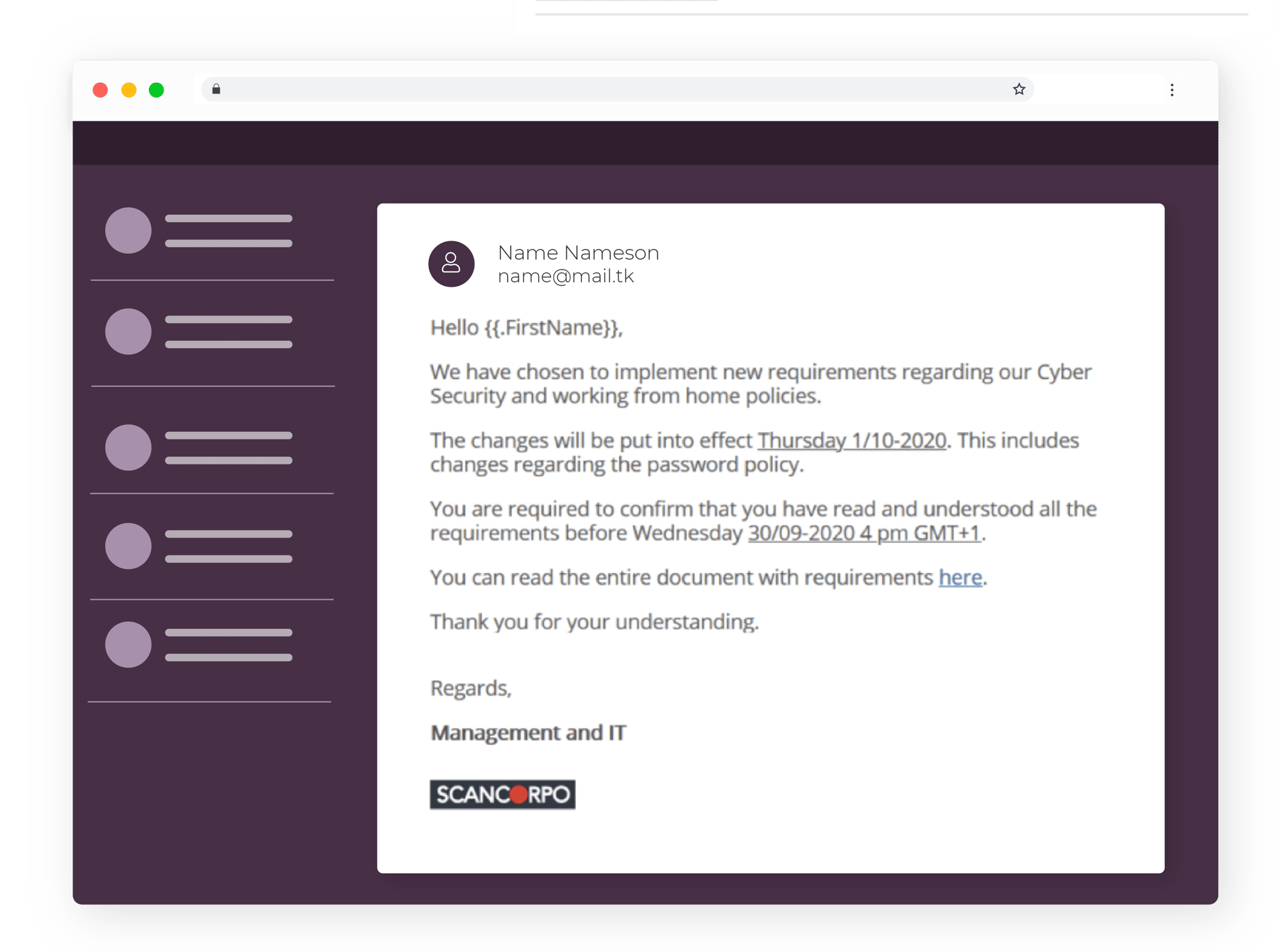
Password policy
This e-mail indicates that the company has a new password policy and all staff must confirm that it is read and understood. It takes advantage of the authority of the company.
Difficulty: 🐟🐟🐟🐟🐟
Phishing giveaways:
- The sender is not a person - just the company
- Changes in response policies despite no warnings
- Short deadline
- Why would you have to login to read this type of information?
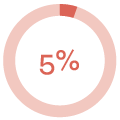
How the campaign performed:
 |
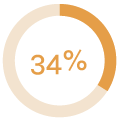 |
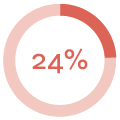 |
| E-mails sent | Links clicked | Submitted data |
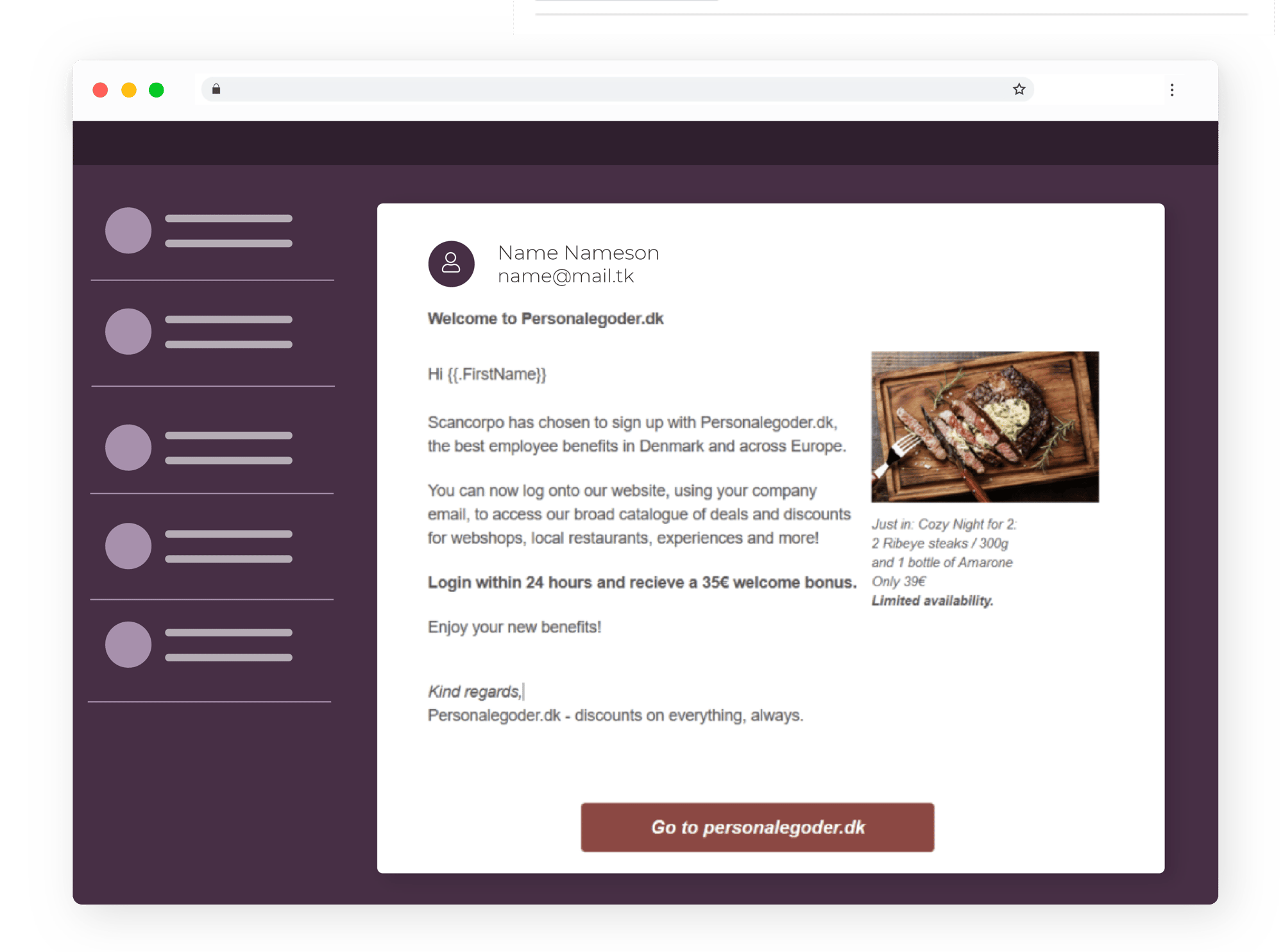
Employee benefits
This e-mail tells the reader that their company has partnered with a discounts website. This means that staff can get a discount on several products if they log in with their work e-mail. It takes advantage of the joy of discounts.
Difficulty: 🐟🐟🐟
Phishing giveaways:
- The website doesn’t exist
- Multiple mentions of limited gifts and discounts
- Asks for your work email
- The sender is suspicious
- The picture looks like a stock photo
How the campaign performed:
 |
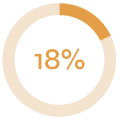 |
 |
| E-mails sent | Links clicked | Submitted data |
Galactic Cloud
This campaign tells the receiver that he/she has received a new file which needs to be opened within 24 hours. If the deadline is not met then his/her access will be removed. The campaign takes advantages of peoples natural curiosity and it has quite a professional look.
Difficulty: 🐟🐟
Phishing giveaways:
- Galatic Cloud is not a real company
- The domain which the e-mail is sent from, info@galacticclouds.com, doesn’t exist either
- It’s unusual that you would receive a file in a cloud-service which you’ve never heard of
- Short deadline for clicking the e-mail
- If you click the link the URL is very suspicious
- It is unusual to receive files from an unknown cloud service
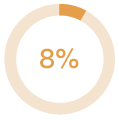
How the campaign performed:
 |
 |
 |
| E-mails sent | Links clicked | Data submitted |
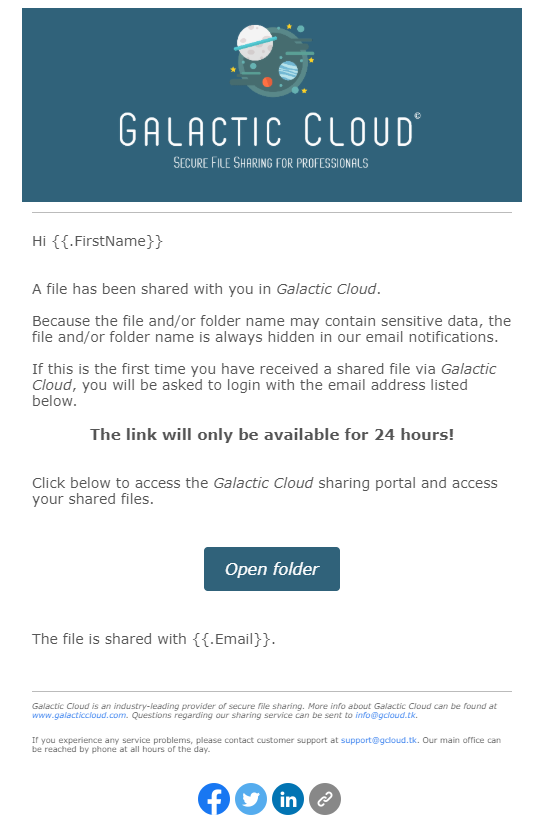
An example of a specific phishing campaign and the actual statistics
Our case study has an example of a phishing mail that we sent through our phishing training. See how many fell for the trap!

You will receive inspiration, tools and stories about good cyber security practices directly in your inbox. Our newsletter is sent out approximately once a month.
