Guide: Getting ISO 27001 Certified Or An ISAE 3402 Security Report
Introduction: What kind of security report should I get?
At CyberPilot, we are seeing that it is a growing requirement for organisations to be certified in information security or to obtain a security audit for ISO 27001 or ISO 27002.
This blog post will provide an overview of the various ways to get certified for information security. You will also learn the difference between different types of security certifications and security audits, and the steps you have to take to obtain each. After reading this post, we hope you will better understand whether you should work towards certification. If you are looking to ensure that you are following the GDPR’s requirements for handling personal data, take a look at the benefits of an ISAE 3000 report.
This post has a lot of information, so here’s what you can expect. First, we will define the different types of certifications and security audits available for information security. In the sections after, we will discuss the pros and cons of each, weigh the potential costs, and finally, give a recommendation for how your organisation could proceed.
Contents
-
Why become ISO 27001 certified or get an ISAE 3402 security audit anyway?
-
What is the difference between ISAE 3402 Type 1 and Type 2 reports?
Why become ISO 27001 certified or get an ISAE 3402 security audit anyway?
Getting certified or audited is a good way to show your clients and partners that your organisation is committed to good IT security practices. It also shows that you are in control of things and are proactive about your organisation’s security.
It can also improve your organisation’s reputation and can be used in marketing campaigns, depending on your industry and context. For example, if you are a company that regularly processes confidential data, then a certification will undoubtedly put your potential customers at ease.
Besides holding an ISO certification, training your team is one of your strongest IT security defenses, with people being the largest security risk for organisations. If you want to know more about how an educated team can boost your IT security, check out our awareness training.
We understand that there are many aspects to consider when you are deciding on a security certification. In the following sections, we will try to further narrow it down for you. If you'd like, you can also start by reading our general guidelines for staying compliant with the GDPR.
What is an ISO Certification?
The International Organization for Standardization (ISO) is an international standard-setting organisation. It is the world’s largest and most widely recognised developer of voluntary international standards. When it comes to information security management, we are concerned with standards in the ISO 27000 family.
The ISO 27000 family (also known as series) consists of information security standards, published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), which is why you will often see the two abbreviations being used. In other words, ISO 27000 and ISO/IEC 27000 are the same standard. Moving forward, we will mostly use the ISO abbreviation, and this will also apply to ISO/IEC 27001 and ISO/IEC 27002.
The series consists of more than a dozen standards. ISO 27000 provides an overview and the vocabulary used in all the standards. Most organisations are concerned with an ISO 27001 certification with the possibility of extending it to ISO 27002.
ISO 27001 is the most widely known standard that provides requirements for an information security management system (ISMS). When companies talk about getting an ISO certification in information security, this is what they are usually referring to. It contains all the policies and processes relevant to how data is controlled and used. However, it does not define specific tools, solutions, or methods. Instead, it functions as a compliance checklist. The main objective is that the work should be an ongoing process, not something that you do only once. Therefore, we focus on how the process and improvements are continuous.
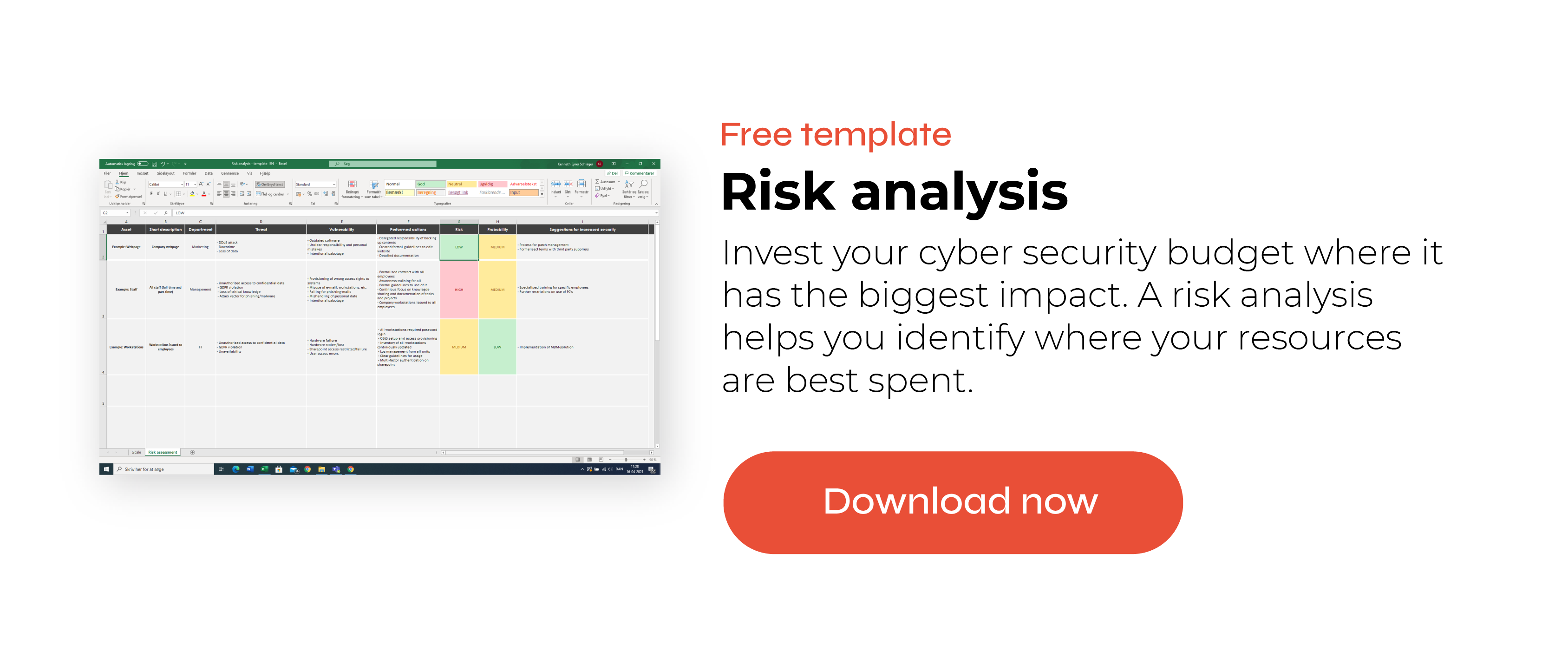
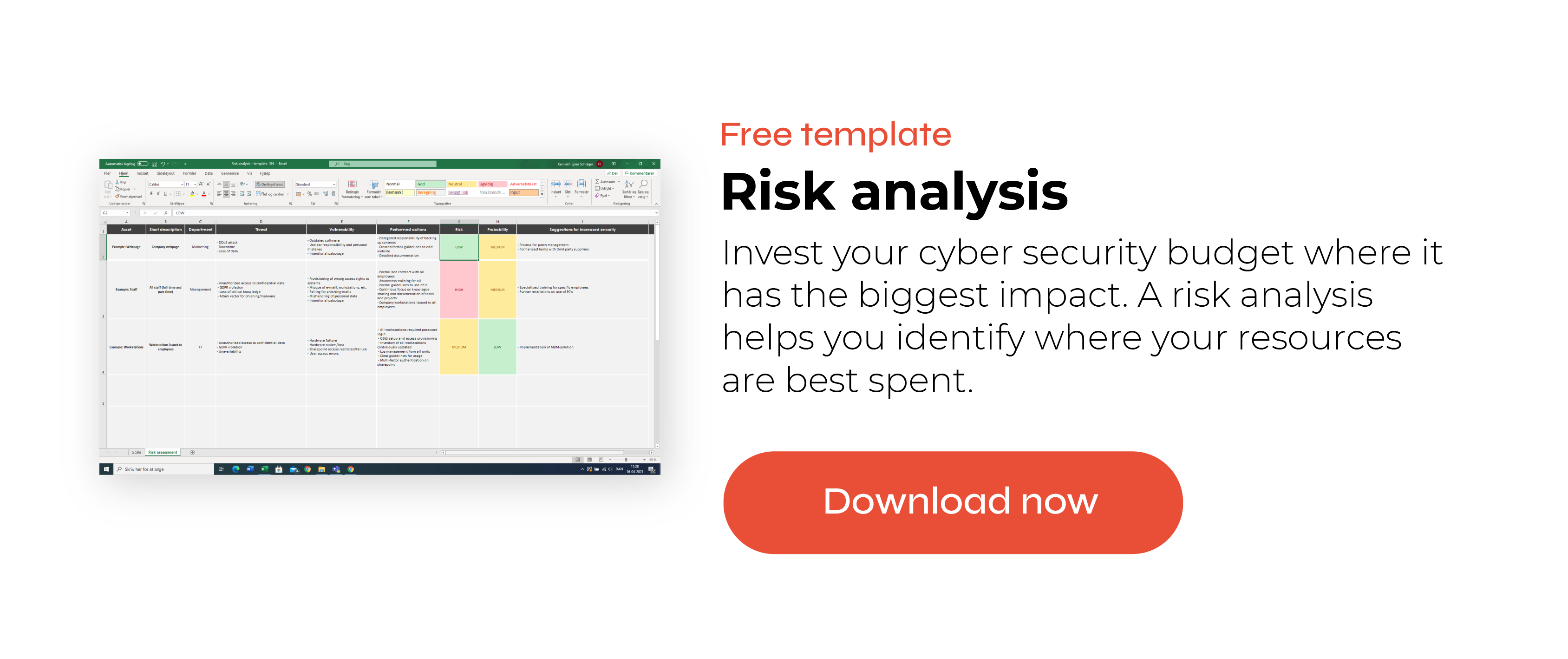
The ISO 27001 uses a risk-based approach, which is why there are no specific or predetermined requirements for an organisation to fulfill. However, with ISO 27001, you are required to implement appropriate technical and organisational measures. Therefore, it is up to the individual organisation to assess what these appropriate measures are. The key here is doing a risk assessment, so you know what measures would be appropriate for your organisation.
Assessing potential security risks can also help you better foresee incidents and plan how to reduce potential risks. Use our guide and free template to create a risk analysis and you are one step on the way to becoming certified.
ISO 27001 requirements
The ISO/IEC 27001 includes ten short clauses and Annex A, which describe how to comply with the standard.
The clauses of ISO/IEC 27001:2022 are:
-
Scope
-
Normative references
-
Terms and conditions
-
Context of the organisation
-
Leadership
-
Planning
-
Support
-
Operation
-
Performance Evaluation
-
Improvement
Additionally, ISO 27001 consists of Annex A, which defines 18 individual areas of information security that organisations should work with, including:
-
Access control
-
Human resource security, including awareness training
-
Networks, including vulnerability scans
-
Physical and environmental security
-
Log management
In short, Annex A is a best practice guide. It has controls you can use to compare the measures your organisation has implemented with the ISO 27001 standards. If your organisation is missing one of the controls, you are expected to either implement it or document the reasons why it is not applicable to your organisation.
An information security management system (ISMS) provides organisations with a systematic approach for managing their information security. It is a centrally managed framework that uses risk management to help you manage your organisation’s information. An ISMS contains all policies and processes relevant to how data is controlled and used.
The overall objective of an ISMS is to define and control the risk levels relevant to an organisation. There are three main areas to consider:
Confidentiality: the data can only be accessed by authorised people
Integrity: the data is accurate and complete
Availability: the data can be accessed when required
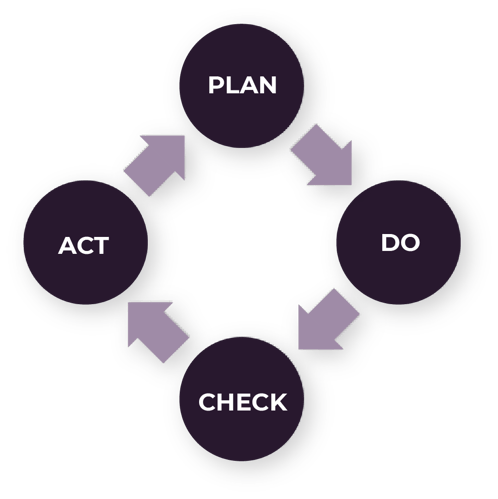
According to ISO 27001, the implementation of an ISMS follows a Plan-Do-Check-Act (PCDA) cycle for continuous improvement. This is an easy-to-use model that helps organisations avoid making repetitive mistakes. We recommend following our guide on applying the Plan-Do-Check-Act (PCDA) model for any sort of process that you want to improve, however, we believe it to be especially useful within IT security.
What is ISO/IEC 27002?
ISO 27002 is not a standard, but a code of practice that offers suggestions, rather than requirements for effective ISMS management. It is less comprehensive than ISO 27001 and does not include the Plan-Do-Check-Act cycle. Normally, it is used by organisations that are already in the process of getting ISO 27001 certified.
ISO 27002 guides organisations in selecting, implementing, and managing controls in their information security risk environment. It is designed to be used by organizations that intend to:
-
Select controls within the process of implementing an ISMS based on ISO 27001.
-
Implement commonly accepted information security controls.
-
Develop their own information security management guidelines.
So, if you are working on getting ISO 27001 certified, the generic controls outlined in ISO 27002 can help you figure out how to customise security guidelines for your own organisation.
What is an ISAE 3402 Report?
The International Standard on Assurance Engagements 3402 (ISAE 3402) is an international assurance standard that prescribes Service Organization Control (SOC) reports. These reports give assurance to organisations’ customers and partners that they have adequate internal controls when it comes to information security. ISAE 3402 defines two types of reports: Type 1 and Type 2.
A Type 1 report includes a review of the documentation, but without the control of the implementation itself. In other words, a Type 1 statement is a snapshot of a given date.
The cost of an ISAE 3402 Type 1 report consists of two parts:
-
The internal preparation, implementation, and documentation.
-
The review, preparation, and ongoing maintenance of the statement. This task must be handled by an authorised information auditor.
The cost will vary depending on the auditor and scope of the report.
A Type 2 report includes a review of the documentation and the verification of the implementation. Typically, this verification will be in the form of samples as well as a review of the documentation and systems. A Type 2 report typically covers a period of 6 or 12 months and aims to show how controls have been managed over time. Therefore, it is more comprehensive than a Type 1 report.
The cost of an ISAE 3402 Type 2 report consists of three parts:
-
The internal preparation, implementation, and documentation.
-
The ongoing work of complying with and documenting the controls.
-
The review, preparation, and ongoing maintenance of the statement.
The cost will vary depending on the auditor and scope of the report.
What is the difference between ISAE 3402 Type 1 and Type 2 reports?
Normally, organisations’ external partners will require a report, but will not specify if it should be a Type 1 or Type 2 report. It is also quite common for organisations to first prepare a Type 1 report and then extend it to a Type 2 report.
Our experience shows that by working towards a Type 1 report and then ‘upgrading’ it to Type 2 report, you get to mature your organisation’s documentation and processes before reaching a Type 2 report. On the other hand, if you start out by trying to obtain a Type 2 report, then you risk having remarks on the report if the documentation and controls do not meet the auditor’s requirements. With a Type 1 report, you can put the processes ‘on hold’, adapt the documentation and processes, and then get audited again.
Another advantage of obtaining a Type 1 report first is that you can get it in a relatively short amount of time since it does not look at the documentation and processes over time. This aspect significantly affects the cost of obtaining a report, and we recommend getting a comprehensive price estimate from the auditor.
Here is our recommendation
For the reasons above, CyberPilot recommends that in most cases, you should work to get an ISAE 3402 Type 1 report first, then extend it to a Type 2 report if necessary. The benefits include:
-
It is significantly less costly to obtain a Type 1 report (up to two times less expensive).
-
You have the opportunity to mature and improve your organisation’s processes and documentation before deciding if you would like to extend it to a Type 2 report.
-
It is faster to get a Type 1 report. A Type 2 report will take 3-6 months, during which time you must still be in operation while being audited.
-
As many external partners will not specify whether they expect a Type 1 or Type 2 report, you can ‘settle’ for a Type 1 report in most cases.
We understand that you may still want to get a further overview of what it takes to get a full ISO certification and see how it compares to getting an ISAE 3402 report. In the next section, we will dive deeper into the reasons why your organisation may want to pursue getting certified or audited and provide roadmaps for both options.
Should I even get ISO certified or a security audit at all?
First, we must determine if it is a priority for your organisation to be certified or to have a security audit.
The reason(s) you may want to get certified could be:
-
It is a legal requirement.
-
It is required by external parties (often, customers or partners).
-
It is required by the board or company owners.
Since preparing to be certified or audited takes a significant amount of time and resources, it is important that you have identified the need to move forward before you begin.
However, we have seen that the process towards a certification or an audit is very valuable for most organisations because it forces them to thoroughly evaluate their information security. During the process, you can become aware of issues that you would normally not address because you didn’t need to do so for an audit or certification. Addressing these issues will undoubtedly create value for your organisation in the long run.
Should I get an ISO Certification or an ISAE 3402 Report?
Next, we discuss whether you should go for a full ISO certification or if you can ‘settle’ with the simpler (and less costly) ISAE 3402 audit report.
A full ISO certification requires that there be a fully implemented ISMS that is documented and observed daily. This is a demanding process at every stage: implementation, operation, initial certification, and ongoing certification.
An ISAE 3402 report is given if the organisation has complied with a specific standard. That means it is still required to show documentation in daily operations, but to a significantly lesser extent than with a full ISO certification. Much of the process of getting an ISAE 3402 report is included in the certification process.
Thus, there are still requirements for both documentation and daily operation, but to a significantly lesser extent than with a full ISO certification. This is also seen in the certification process itself, which for an audit consists of samples and interviews.
The cost of a full ISO certification and security audit will naturally vary from organisation to organisation, depending on several parameters, such as the scope, maturity of the organisation’s information security, internal resources, and competencies. As a starting point, it is expected that a full ISO certification will cost 4-5 times more than an audit statement (inclusive of all stages).
In general, we have seen that full ISO certifications are very limited in use in the EU and security audits are much more common. This can be seen as a statement that the market often deems audits to be sufficient. It is typically only very large corporations that aim for full ISO certification.
When deciding on whether to obtain a full certification or security audit, one should also consider the tasks both processes entail.
It can be difficult to explain which exact tasks are associated with implementing and maintaining the certification/report, as they will differ between organisations. However, we will start by illustrating the steps involved for the path we recommend for most organisations:
ISAE 3402 Assurance Report – Type 1 in relation to ISO 27002
The later sections in this blog post will further outline what is required to go from an audit to a full certification.
What is required for getting a ISAE 3402 Type 1 report?
The following documentation must be available for review before the report can be prepared by the auditor.
-
Overall information security policy (statement from management), which contains objectives and responsibilities.
-
Documentation of risk assessment – documentation that this process has been completed and approved by management.
-
The information security handbook, which describes the overall process and measures at a high level. The manual follows chapters from the ISO 27002 standards. The information security handbook is for documentation of the measures that have been implemented to handle information security. It is a document for use in the IT department and for auditing, not for general staff.
-
Policies, guidelines, and procedures relating to information security. E.g., a contingency plan and guidelines for employees.
Since ISO 27002 is a risk-based approach, it will also be relevant to look at the conclusions from your risk assessment and determine which improvements must be made to achieve an acceptable risk level.
Next, we will discuss the steps required to ‘upgrade’ to a Type 2 report and then to an ISO 27001 certification.
What is required to get an ISAE 3402 Type 2 Report?
To get a Type 2 report, you will mostly need the same type of documentation as you need for a Type 1 report. Here are other things to expect:
- Preparation - the organisation and description of the controls.
- Ongoing control and documentation of activities (time interval must be determined).
- Cost of the audit statement – up to two times more compared to a Type 1 report.
A significant amount of time and cost should be expected to extend your report to a Type 2 report. This goes for the preparation, ongoing inspections, and cost of the auditor. There is also a risk that the auditor will object to the newly implemented control, which may mean you will have unfavourable findings in the report.
Discuss the possibilities with your auditor
We recommend that you initiate a dialogue with the auditor about a future desire to get a Type 2 report while beginning the process of getting a Type 1 report. In this process, it will become clearer which additional measures and controls you will have to implement in order to obtain a Type 2 report. Additionally, the auditor will also have a better idea for estimating the efforts required to extend the report. By taking a step-by-step approach, you can often significantly reduce the cost of having an auditor.
This is a typical roadmap for getting a security audit
- Determine the scope of the security audit with selected clients and partners. The purpose is to ensure that both parties accept the intended levels of review.
- Initiate a dialogue with the auditors to get an estimated cost for their preparation of the security audit.
- Come to a final decision on the type of security audit and its level of review.
- Gather the relevant documents, which include:
- The organisation’s information security policy
- The information security manual
- Additional guidelines and policies that can be relevant.
- Agree with the auditor about the preparation of the security audit.
- Implement the new processes.
- The Type 1 security audit is performed.
- The new Information Security Management System (ISMS) is operating for 6-12 months.
- It is possible to perform a Type 2 security audit.
How to go from ISO 27002 to ISO 27001
The difference between ISO 27001 and ISO 27002 is in the documentation and the establishment of the management system, including the PDCA cycle. It is this part that must be implemented and operated to go from ISO 27002 to ISO 27001. In ISO 27001, chapters 4-10 must be included in the organisation’s management system for information security.
The steps required to establish this process lie partly in the documentation and organisation of your internal processes for the four phases, and partly in the time it takes your organisation to implement the processes.
The real difference lies in the ‘check’ and ‘act’ phases of the PDCA. Here, ISO 27001 requires that a continuous process is used to set objectives for the individual initiatives, check if the initiatives are effective, and continuously make adjustments if the results deviate from the objectives.
As ISO 27001 has a larger scope than ISO 27002, it can be expected that the audit will cost significantly more, as the auditor will also review and revise the documentation from Chapters 4-10 as part of the certification process.
Here is what you can expect:
- Preparation – Documentation and description of processes covered in chapters 4-10 of the ISO 27001 standard.
- Implementation and the processes associated with the four phases (Plan-Do-Check-Act).
- Security audit – Should be agreed on with the auditor.
The extra internal time required is the biggest difference in getting from an ISO 27002 to an ISO 27001 certification.
Just like working with an ISAE 3402 Type 1 vs Type 2 audit, it will be to your advantage to work step-by-step when expanding from ISO 27002 to ISO 27001. Getting certified in ISO 27001 may very well be suitable for organisations as they mature.
Why CyberPilot recommends getting an ISAE 3402 report
At CyberPilot, we recommend that the ISAE 3402 report is typically the optimal choice for most organisations to work toward. This is because of the following:
- The additional costs incurred before, during, and after a full ISO certification are likely to exceed its added value. This is not the case with an ISAE 3402 report.
- If you later find that you want to ‘upgrade’ to a full ISO certification, the ISAE 3402 report will still serve as a good starting point.
Note: We ALWAYS recommend that you contact and discuss this decision with the customers and partners who require you to obtain certification or an audit, before you start to work towards it.
CyberPilot, your partner for information security
We hope that this blog post has given you a better understanding of ISO 27001 certifications and ISAE 3402 reports. At CyberPilot, we offer solutions that can help you strengthen the information security in your organisation to prepare for certification or an audit. These solutions include:
If you have any questions about our solutions, feel free to contact us at info@cyberpilot.io. We can help you put your organisation on the right path toward better information security.
You will receive inspiration, tools and stories about good cyber security practice directly in your inbox. Our newsletter is sent out approximately once a month.